Introduction
With countless options for provisioning and configuring infrastructure, it can be difficult to determine the ideal solution. Terraform and Ansible are two of the most sought-after tools in this domain, so let’s compare their distinctions to support you in making a decision in the Terraform vs Ansible debate.
Video
Below is a video explanation.
Video Chapters
You can skip to the relevant chapters below:
- 00:00 – Introduction
- 00:40 – Agenda
- 00:59 – What is Terraform?
- 02:16 – What is Ansible?
- 03:44 – Infrastructure as Code
- 05:17 – Configuration Management
- 06:04 – Infrastructure State
- 07:29 – Mutable Infrastructure
- 08:48 – Immutable Infrastructure
- 10:03 – Idempotence
- 11:43 – Imperative Programming
- 12:26 – Declarative Programming
- 13:08 – Which to Choose?
Overview
When it comes to provisioning and configuring infrastructure, there are a few popular options to choose from. Terraform and Ansible are two of the most well-known tools in this space. But which one is right for you? Let’s take a look at the key differences between Terraform and Ansible to help you make a decision.
In this blog post, we will discuss many concepts of Infrastructure as Code and Configuration Management to understand Terraform and Ansible better. This is part 1 of a 2-part blog series. In part 2, we will demo both Terraform and Ansible to show the differences practically.
What is Terraform and what does it do?
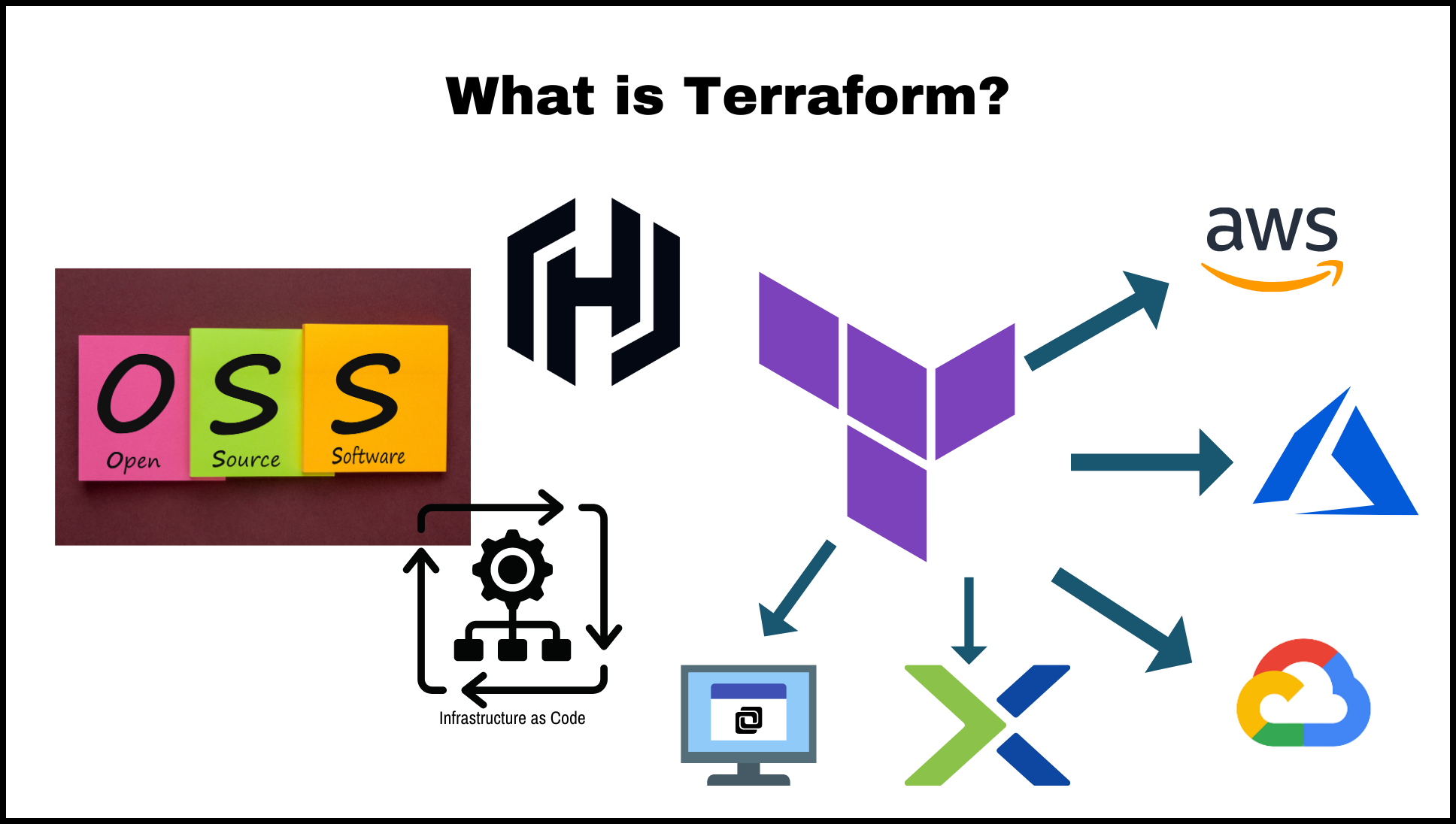
What is Terraform?
Terraform is an open-source infrastructure-as-code software tool that allows you to define and manage resources in a safe and predictable way. It is developed by HashiCorp and is particularly popular for creating and managing infrastructure resources across multiple cloud infrastructure providers, including AWS, Azure, and Google Cloud. It can also be used for existing infrastructure running on-premises on vSphere or Nutanix.
With Terraform, you can use simple, declarative configuration files to describe the resources you need, and then use the Terraform command-line interface (CLI) to create and manage those resources. Terraform can create and manage resources such as virtual machines, network interfaces, and DNS records.
One of the key benefits of using Terraform is that it allows you to version your infrastructure and track changes over time. This makes it easier to collaborate with others and track the history of your infrastructure. Terraform also has a large and active community, which means that there are many resources and plugins available for extending its capabilities.
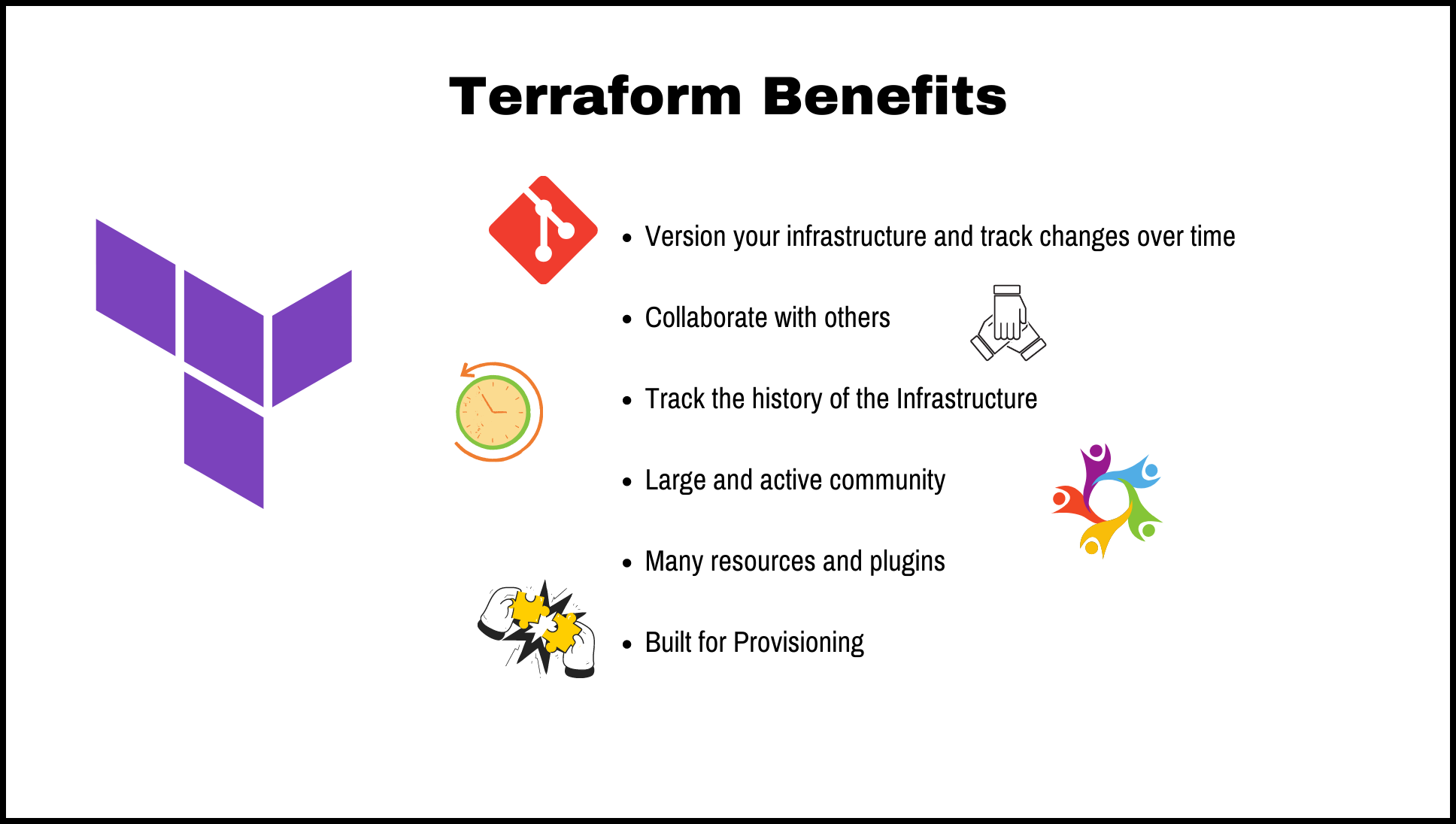
Terraform Benefits
What is Ansible and what does it do?
Ansible is an open-source configuration management and infrastructure management tool that makes it easy to deploy and manage applications in large-scale environments. It automates configuration processes and reduces deployment time, ensuring configuration consistency across all different types of systems, such as virtual machines, network devices, and containers.
Ansible uses an agentless architecture, which means that it does not require any software to be installed on the managed servers. Instead, it uses SSH to connect to the servers and perform tasks.
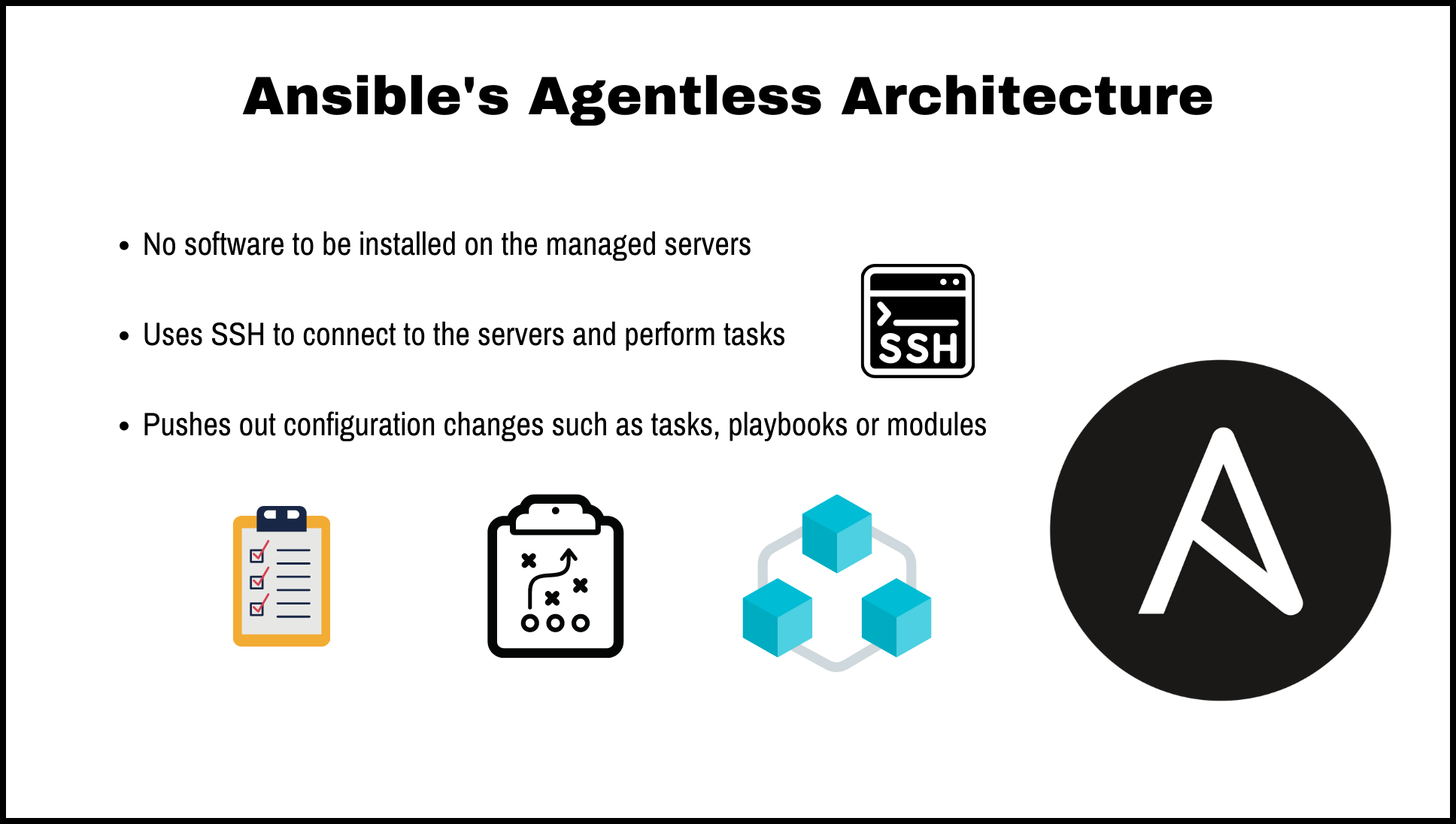
Ansible’s Agentless Architecture
It works by connecting over SSH or Windows Remote Management (WinRM) and pushing out configuration changes such as tasks, playbooks or modules. This makes it much quicker to configure multiple hosts across distributed networks while providing the flexibility to do so without requiring specialized configuration languages.
One of the key benefits of using ansible is that it allows you to automate repetitive tasks and ensure that your infrastructure is consistently configured. It also has a large and active community, which means that there are many resources and plugins available for extending its capabilities.

Ansible Benefits
How are Terraform and Ansible different from each other?
When it comes to Terraform vs Ansible, we still need a bit more clarity on the differences. Let’s take a closer look. Terraform and Ansible are two popular software products used for provisioning infrastructure, but the two tools have major differences between them.
Terraform is a provisioning tool that allows users to create infrastructure and manage it using HashiCorp Configuration Language (HCL). This provisioning is done through Infrastructure as Code (IaC), meaning that it can be versioned and tracked like any other program.
Ansible, on the other hand, uses an agentless architecture which enables system administrators to quickly connect with nodes from Ansible playbooks to perform specific tasks such as setting up configuration or deploying applications. Whereas Terraform generally focuses on provisioning infrastructure itself, Ansible is more directed at provisioning by automating configuration and deployment processes ahead of time.
Both have their own unique strengths in provisioning and configuring infrastructure, making them valuable tools for DevOps teams. Let’s examine some additional terms to understand more.
Infrastructure as Code
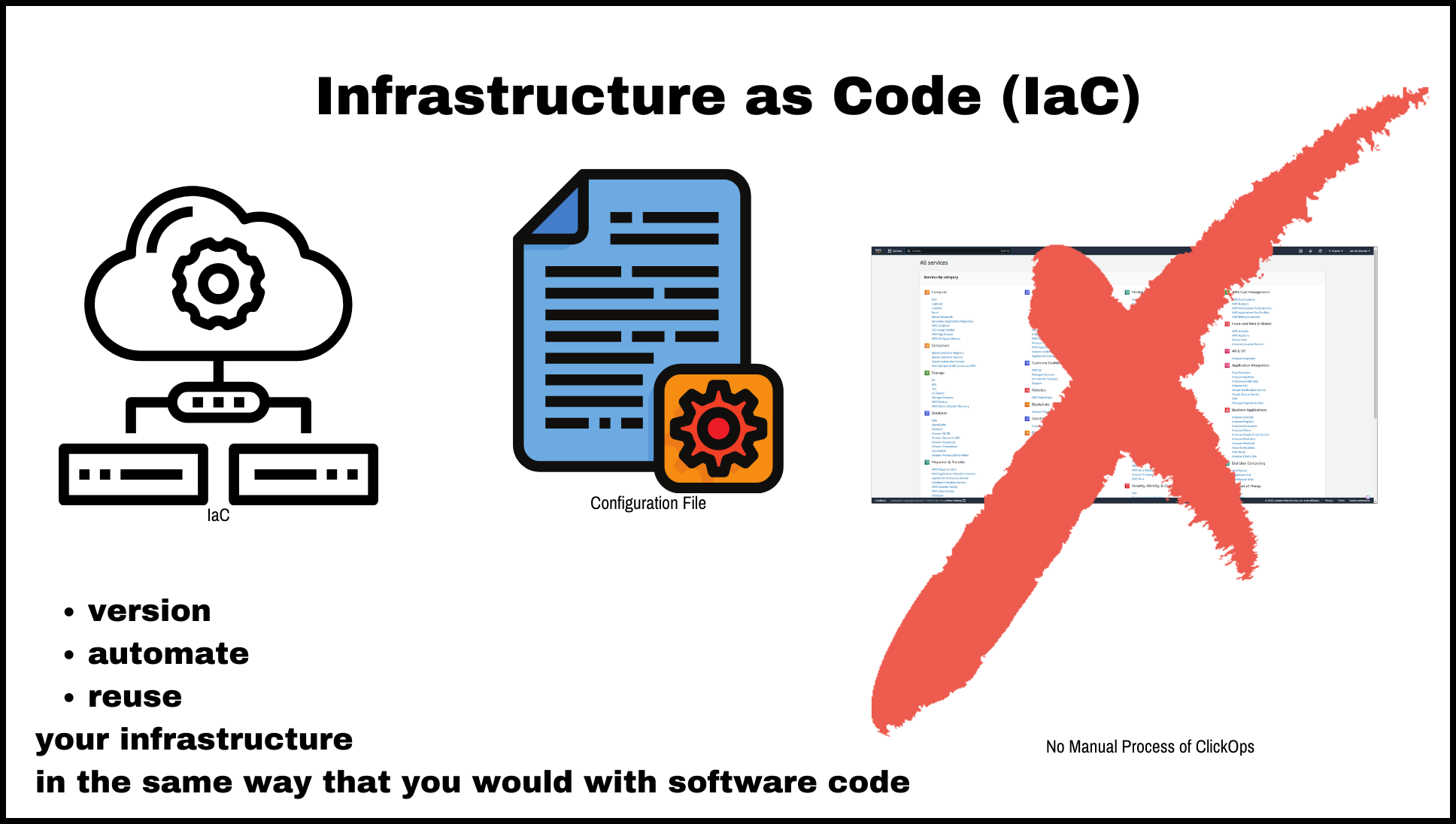
Infrastructure as Code
Infrastructure as code (IaC) is an approach to managing infrastructure in which infrastructure resources are defined and managed using code and configuration files rather than using manual processes. This allows you to version, automate, and reuse your infrastructure in the same way that you would with software code.
Using IaC has several benefits. It allows you to define your infrastructure in a declarative way, which makes it easier to understand and maintain. It also makes it easier to automate the provisioning and management of your infrastructure, as you can use tools to apply your configuration files and make changes to your resources. Additionally, IaC makes it easier to collaborate with others and track the history of your infrastructure, as you can use version control systems to track changes to your configuration files.
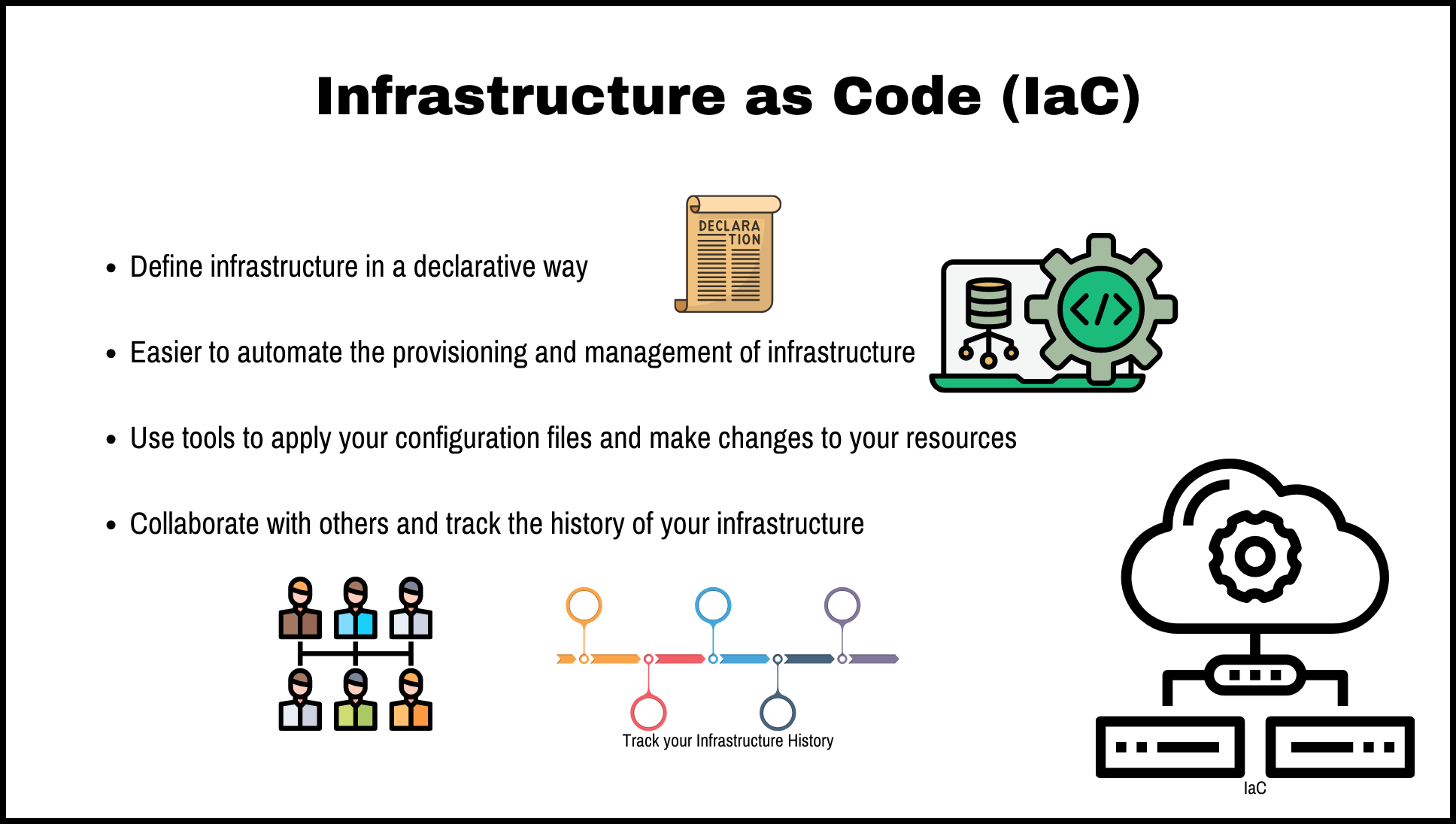
Infrastructure as Code Benefits
Infrastructure as Code Tools
There are a number of tools available for managing infrastructure as code, including Terraform, CloudFormation, and Azure Resource Manager (ARM).
These tools allow you to define your infrastructure using configuration files, and then use the tools’ command-line interfaces to apply those configurations and manage your resources.
Some have added Ansible, Chef, Puppet and the like to this list which has made things confusing. Ansible, Chef, and Puppet are more suited to belong to the configuration management family of tools. Let’s now take a closer look at Configuration Management.
Configuration Management
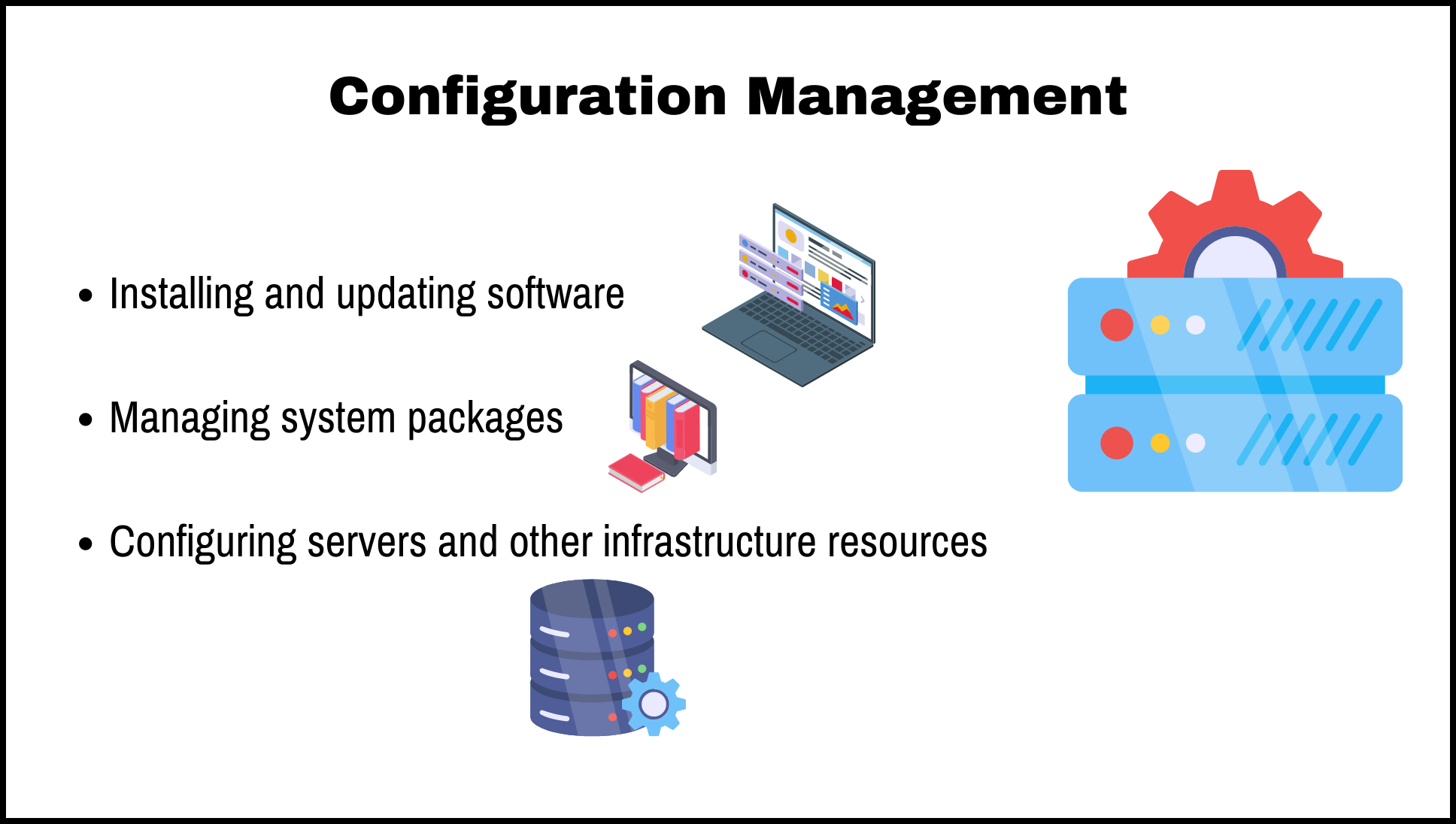
Configuration Management
Configuration management is the process of maintaining and controlling the configurations of resources in an organized and predictable way. This includes tasks such as installing and updating software, managing system packages and configuring servers and other infrastructure resources.
Configuration management tools allow you to automate these tasks and ensure that your infrastructure is consistently configured and up to date. They also provide a way to track changes and roll back if necessary, which helps to reduce the risk of unintended changes and errors.
Configuration Management Tools
Some examples of these tools include Ansible, Chef, Puppet, and SaltStack. These tools allow you to define the desired state of your infrastructure using configuration files or scripts, and then use the tools’ command-line interfaces to apply those configurations and manage your resources. Configuration management tools can be used in conjunction with infrastructure-as-code tools such as Terraform to provide a complete solution for managing and configuring your infrastructure.
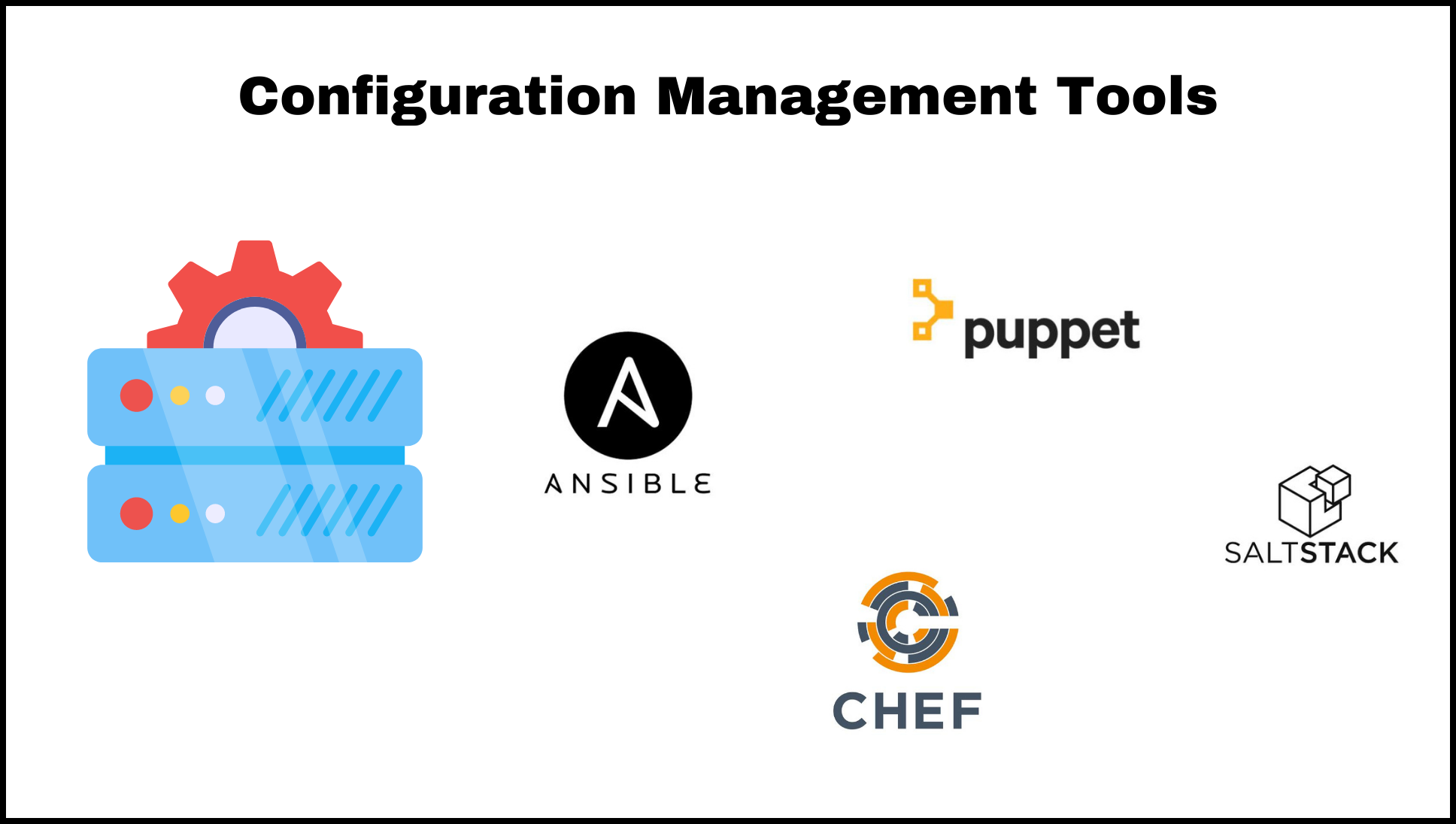
Configuration Management Tools
Storing the Infrastructure State
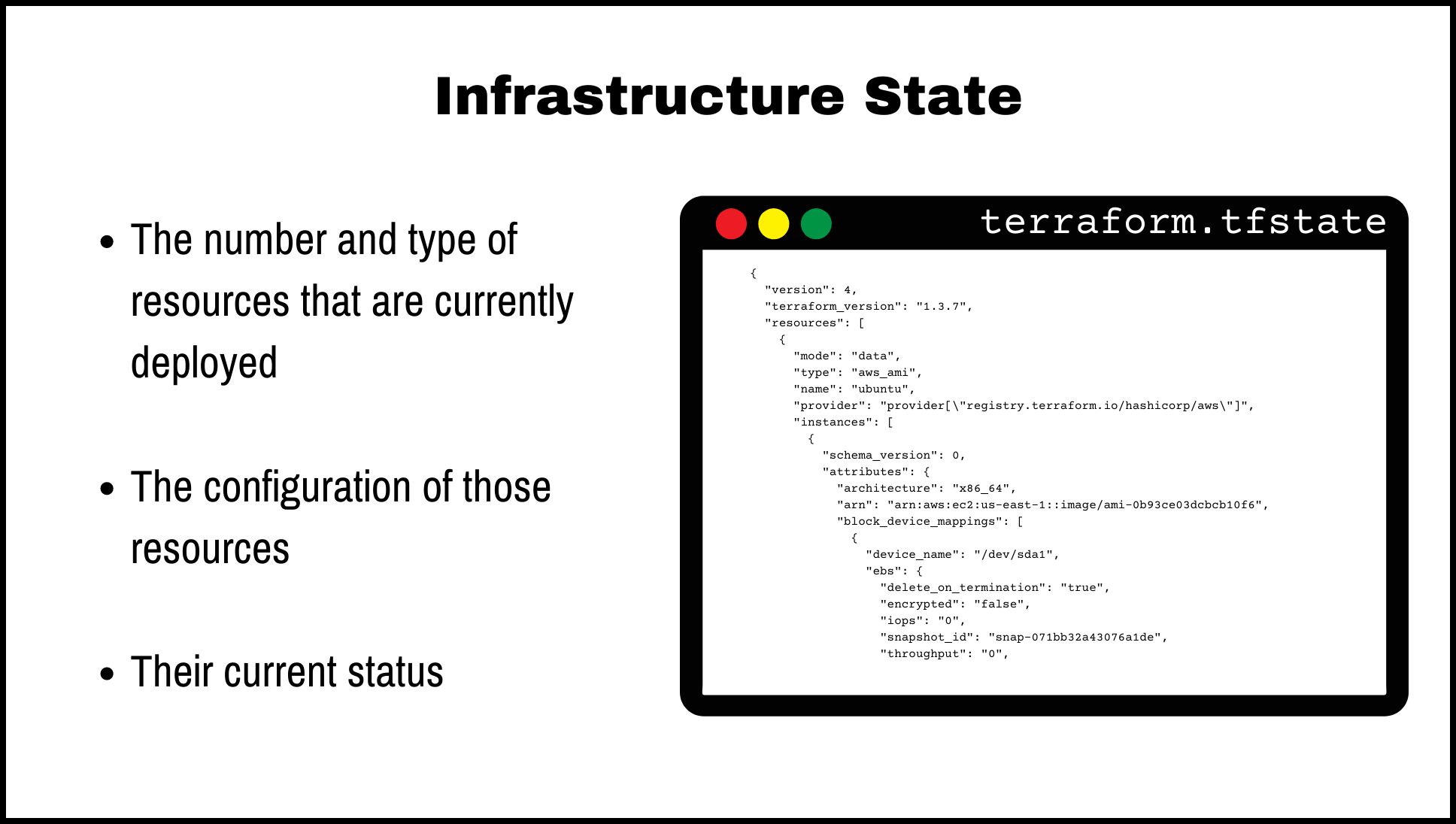
Infrastructure State
In infrastructure as code (IaC), the infrastructure state refers to the current configuration and status of your infrastructure. This includes details such as the number and type of resources that are currently deployed, the configuration of those resources, and their current status.
Tools that support IaC typically provide a way to store the infrastructure state, which allows you to track the current state of your infrastructure and use it as a reference for making changes. This is often done using a state file, which is a file that contains the current state of your resources.
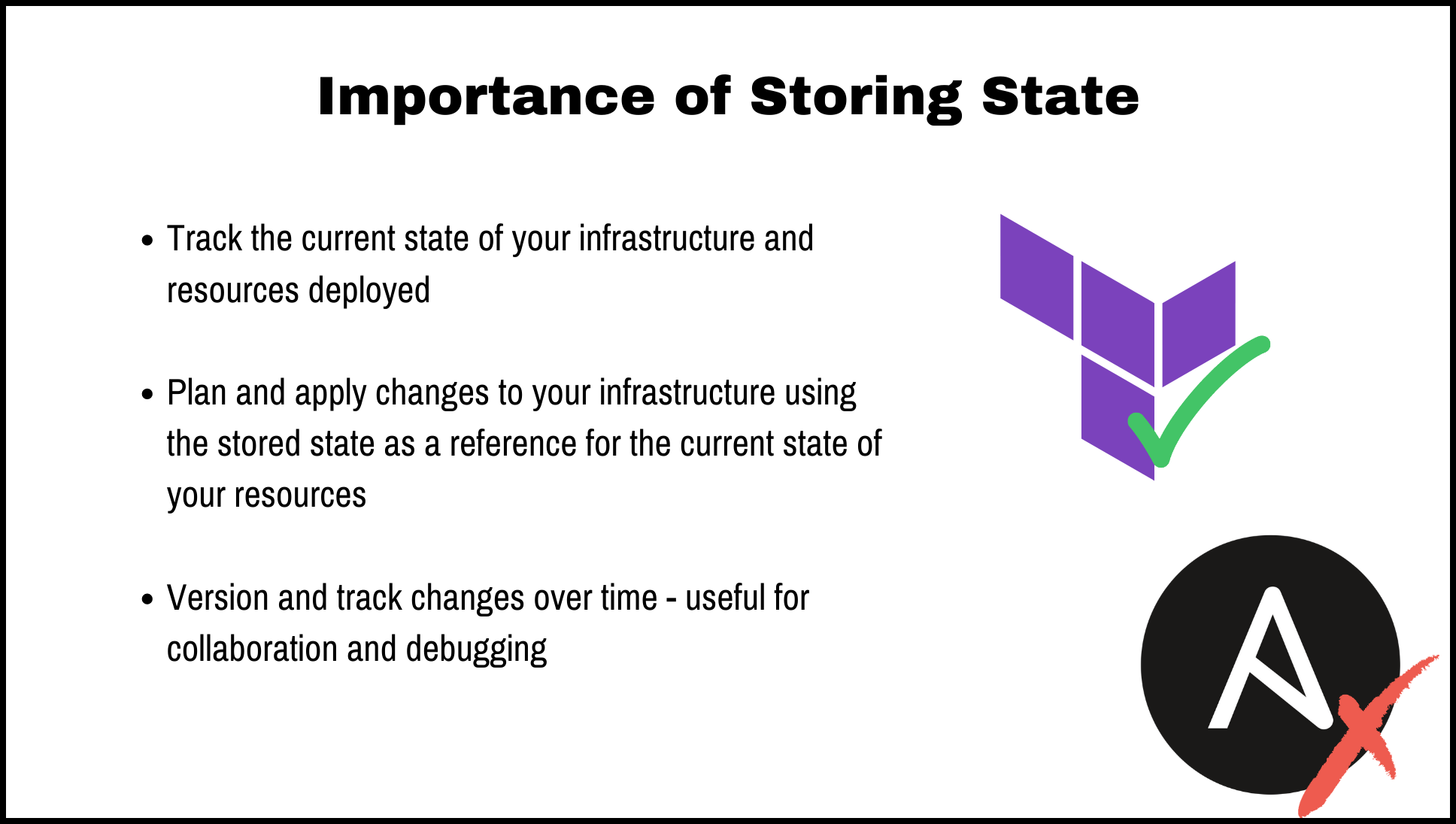
Storing the infrastructure state is important for several reasons. It allows you to track the current state of your infrastructure and understand what resources are currently deployed. It also makes it easier to plan and apply changes to your infrastructure, as you can use the stored state as a reference for understanding the current state of your resources. Storing the infrastructure state allows you to version and track changes to your infrastructure over time, which can be useful for collaboration and debugging.
Importance of Infrastructure State
When it comes to ansible versus terraform, Terraform stores the state of the infrastructure whereas Ansible does not. This gives Terraform an advantage over Ansible because it would take more lines of code to get Ansible to work around the lack of state storage.
Mutable Infrastructure
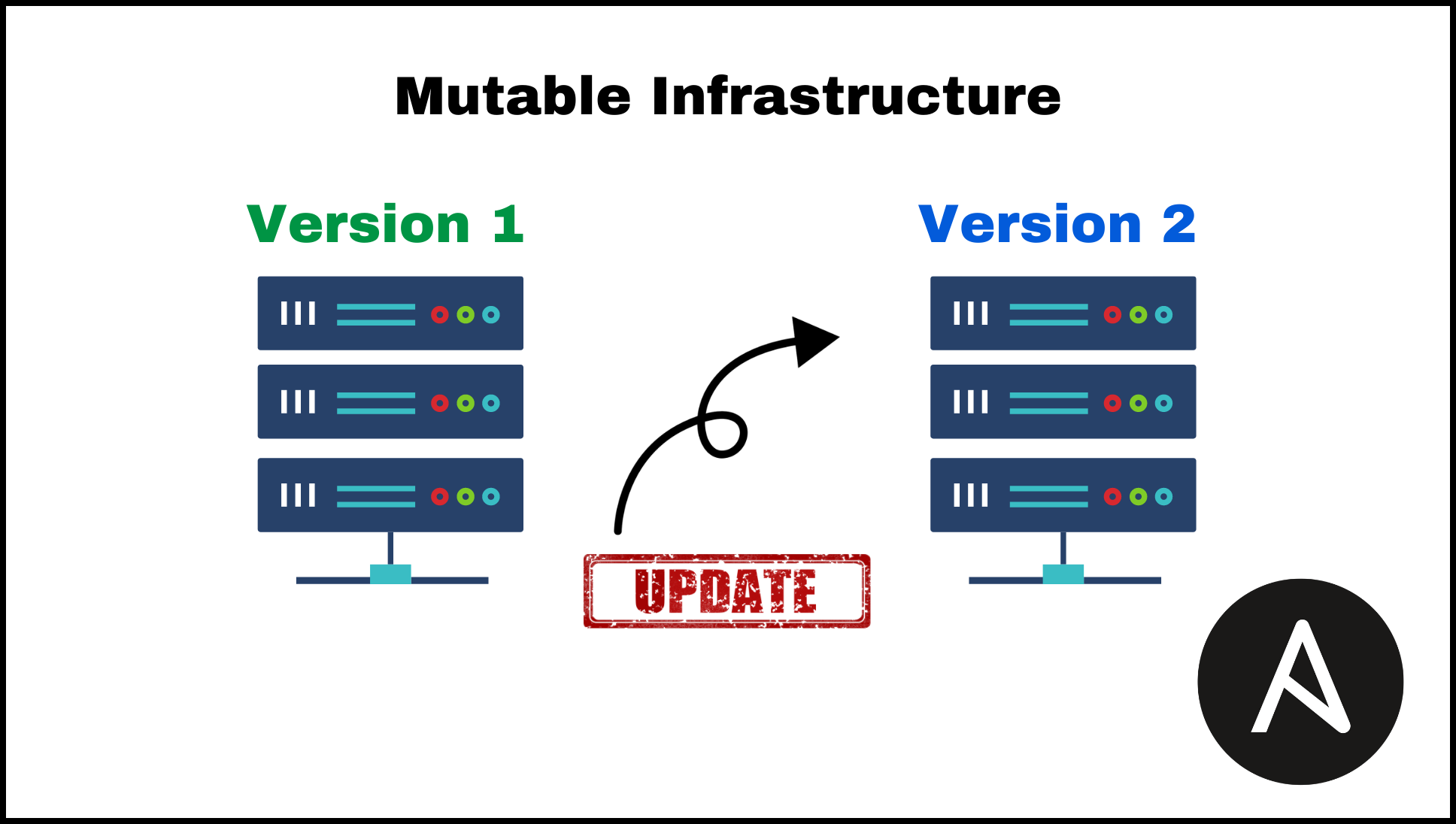
Mutable Infrastructure
Mutable infrastructure is an approach to managing infrastructure in which resources are modified in place rather than replaced. This means that when you want to make a change to an infrastructure resource, you modify the existing resource rather than create a new version of it.
Ansible can be used to help with infrastructure management by providing a way to automate the configuration and management of resources. With Ansible, you can write simple playbook scripts to describe the desired state of your infrastructure, and then use the ansible command-line interface to apply those playbooks to your resources. This makes it easier to manage the configuration of your infrastructure over time, as you can use Ansible to ensure that your resources are consistently configured and up to date.
One of the key benefits of using mutable infrastructure is that it can be easier to manage in some cases, as you can make changes to resources directly rather than needing to recreate them. However, it can also be more difficult to track changes and roll back if necessary, as it is harder to see exactly what changes have been made to a resource. It is also generally considered to be less robust and secure than immutable infrastructure, as there is a greater risk of unintended changes being made to your infrastructure.
Immutable Infrastructure
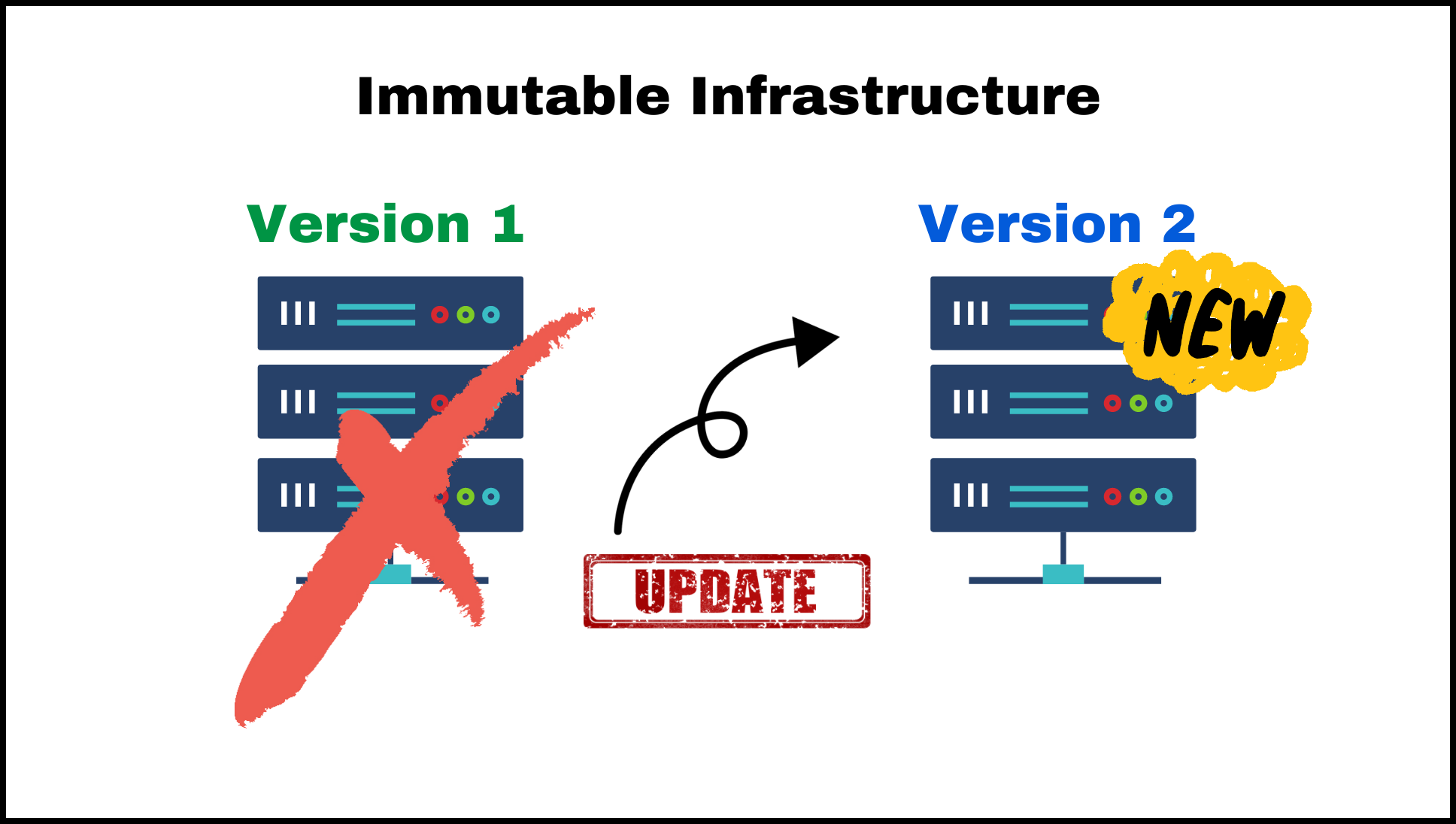
Immutable Infrastructure
The Immutable infrastructure approach is a way to manage infrastructure in which resources are replaced rather than modified in place. This means that when you want to make a change to an infrastructure resource, you create a new version of that resource rather than modifying the existing one.
Terraform can be used to help manage immutable infrastructure by providing a way to define and create resources in a predictable and versionable way. With Terraform, you can use configuration files to describe the desired state of your infrastructure, and then use the Terraform CLI to create and manage those resources. This makes it easier to recreate your infrastructure from scratch if necessary, as you can use your configuration files as a reference for building out your resources.
One of the key benefits of using this approach is that it makes it easier to track changes and roll back if necessary. Since you are replacing resources rather than modifying them in place, it is easier to see exactly what changes have been made and to revert to a previous state if necessary. It is also generally considered to be more robust and secure, as it reduces the risk of unintended changes being made to your infrastructure.
Idempotence
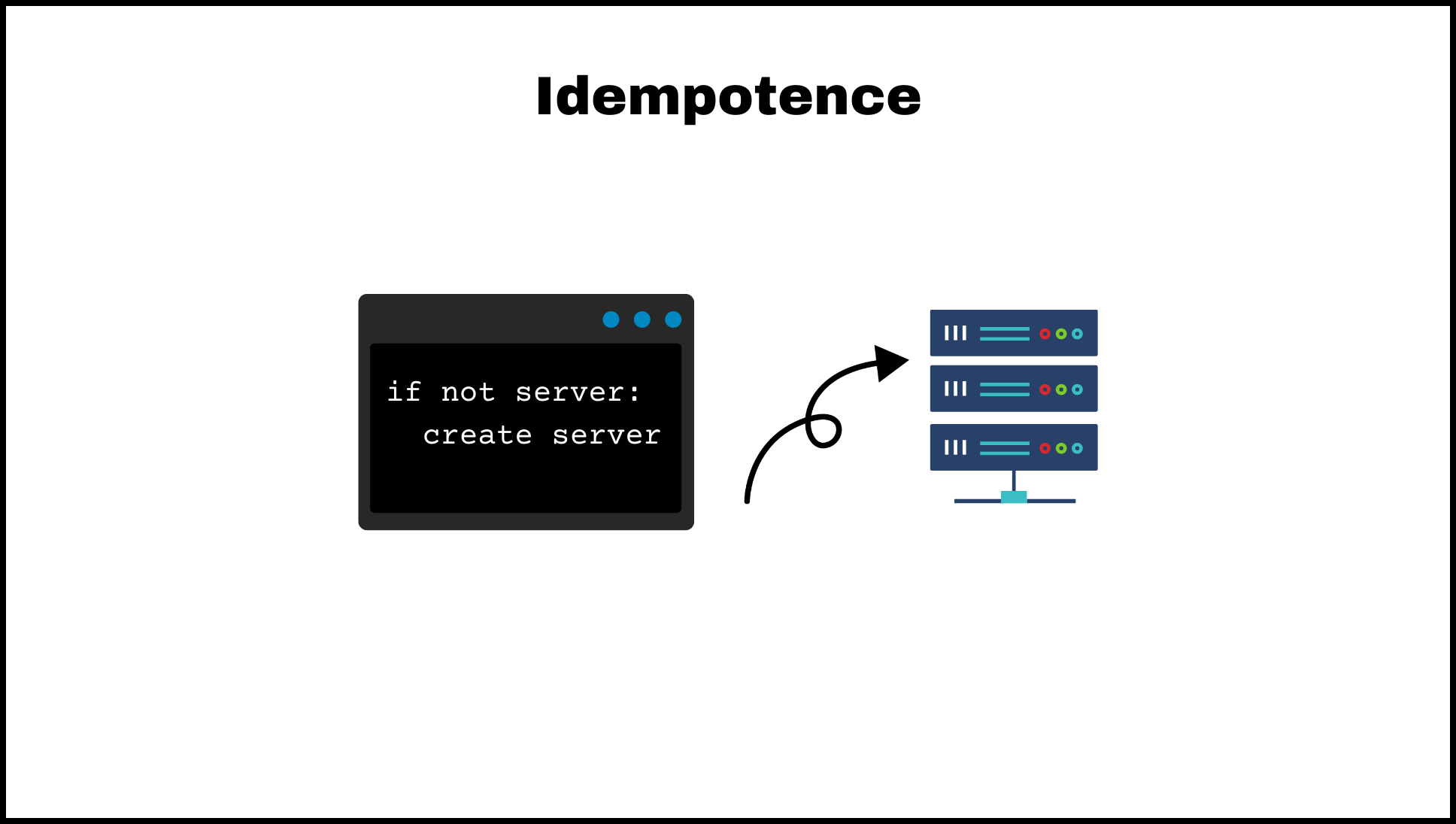
Idempotence
In computer science, idempotent refers to an operation that has no additional effect if it is called multiple times with the same input. In other words, an idempotent operation will produce the same result no matter how many times it is called, as long as the input is the same.
In the context of a configuration management tool like ansible or an infrastructure provisioning tool such as Terraform, idempotence is an important concept because it allows these tools to ensure that the desired state of a system is consistently maintained.
For example, if you use ansible to install a package on a server, and you run the same playbook multiple times, ansible will ensure that the package is installed only once. If the package is already installed, ansible will not try to install it again, because the installation is idempotent. This ensures that the server is not unnecessarily modified and helps to prevent unintended changes or errors.
Similarly, in Terraform, if you use a resource configuration to create an AWS EC2 instance, and you run the same configuration multiple times, Terraform will ensure that only one EC2 instance is created. If the EC2 instance already exists, Terraform will not try to create it again, because the resource configuration is idempotent. This ensures that the desired state of the infrastructure is consistently maintained and helps to prevent unintended changes or errors.
Overall, idempotence is an important concept in configuration management tools because it allows these tools to consistently maintain the desired state of a system and helps to prevent unintended changes or errors. It’s also needed for lifecycle management.
Declarative vs Imperative (Procedural) Programming
Declarative programming and imperative programming are two different programming paradigms that have different approaches to specifying how a program should be executed.
Imperative Programming

Imperative Programming
Imperative programming is a programming paradigm that focuses on specifying how a program should be executed by explicitly defining the steps or instructions that the program should follow.
In imperative programming, the programmer specifies the exact sequence of steps that the program should take to solve a problem, and the program executes these steps in order. Imperative programming languages typically provide control structures such as loops and conditional statements that allow the programmer to specify the exact flow of execution. Examples of imperative programming languages include C, C++, and Java. Ansible falls under this category.
DeclarativeProgramming

Declarative Programming
Declarative programming is a programming paradigm that focuses on specifying what a program should do, rather than how it should be done. In declarative programming, the programmer specifies the desired outcome or result of the program, and the program determines the best way to achieve that result. Declarative programming languages typically do not provide explicit control structures for specifying the flow of execution, and instead, rely on the programmer to specify the desired result and let the language or runtime determine the best way to achieve it. Examples of declarative programming languages include SQL, HTML, and Terraform.
So the main difference between declarative programming and imperative programming is the way in which the programmer specifies the behaviour of the program. In imperative programming, the programmer specifies the exact steps that the program should take to solve a problem, while in declarative programming, the programmer specifies the desired result and lets the language or runtime determine the best way to achieve it.
Which one should you use for your infrastructure needs – Terraform or Ansible?

Decision
Terraform and Ansible are both popular tools for managing infrastructure, but they serve different purposes. Terraform is an infrastructure-as-code tool that allows you to define and manage infrastructure resources in a safe, declarative way. It is particularly useful for creating and managing cloud infrastructure across multiple cloud providers.
Ansible is a configuration management tool that helps with infrastructure automation. It is particularly useful for tasks such as installing software, updating configuration files, and managing system packages.
In general, you would use Terraform to create and manage your resources, and then use Ansible to configure and manage those resources once they are up and running. However, it is also possible to use both tools together, as Terraform can be used to set up the infrastructure and pass information about the created resources to Ansible for further configuration. Check this blog post called Jenkins, Vault, Terraform, Ansible, and Consul Delivering an End-to-End CI/CD Pipeline. It’s the last part of a 4 part series on how to deploy an application in production with best practices. I explain and demo how to use both Terraform and Ansible together in conjunction with Jenkins as the CI/CD pipeline tool.
Conclusion
In conclusion, both Terraform and Ansible are DevOps tools that can help you with the infrastructure management process. They both allow you to automate infrastructure provisioning. However, they differ in their approach. If you need more control over your infrastructure or want to use immutable servers, then Terraform is the tool for you. On the other hand, if you need something that is more flexible or agentless, then Ansible is the better choice. Ultimately, the decision of which tool to use depends on your specific needs and preferences. Many customers that I’ve worked with actually use both.
I write quite a bit about IaC. If you’re interested in Terraform, check out the Terraform 101 course on the TeKanAid Academy site. You could also take a look at some of the blog posts such as this one Terraform to Create a Ubuntu 22.04 VM in VMware vSphere ESXi or the Terraform Import Example – AWS EC2 Instance post.
Stay tuned for part 2 where I demo both Terraform and Ansible to show the differences discussed in this blog post.
Suggested Reading
- Terraform vs Ansible – Demo the Differences – Part 2
- Terraform Import Example – AWS EC2 Instance
- Build a Kubernetes k3s Cluster in vSphere with Terraform and Packer
- HashiCorp Packer for VMware Ubuntu Templates and Terraform for building VMs
- DevOps Engineer NOT on Linux? Check out WSL2
- AWS Lambda – Terraform Example with API Gateway
- env0 – A Terraform Cloud Alternative
- Crossplane: Unveiling a New Horizon in Cloud Infrastructure Management