Introduction
Software is at the heart of innovation for today’s enterprises, transforming every business into a software business. Organizations including the world’s largest global companies are making a shift from monolithic applications to highly distributed, cloud-native microservices. This is made possible by the modern cloud, container, and orchestration technologies, such as AWS, Docker, and Kubernetes. In this article, we show 3 demos that take us through the life cycle of microservices applications.
The Challenge
The key challenge that enterprises face as they shift to highly distributed, orchestrated environments is a loss of visibility needed to understand and solve issues in this new dynamic environment. The Sysdig Cloud-Native Visibility and Security Platform closes the cloud-native visibility gap, giving a consistent way to manage the risk, health, and performance of systems, applications and microservices within and across clouds.
With Sysdig, the world’s largest enterprises solve a broad array of use cases for cloud-native environments to deliver 3x faster cloud-native transformation, a 67% increase in DevOps efficiency, and a 95% reduction in risk.
The Demos
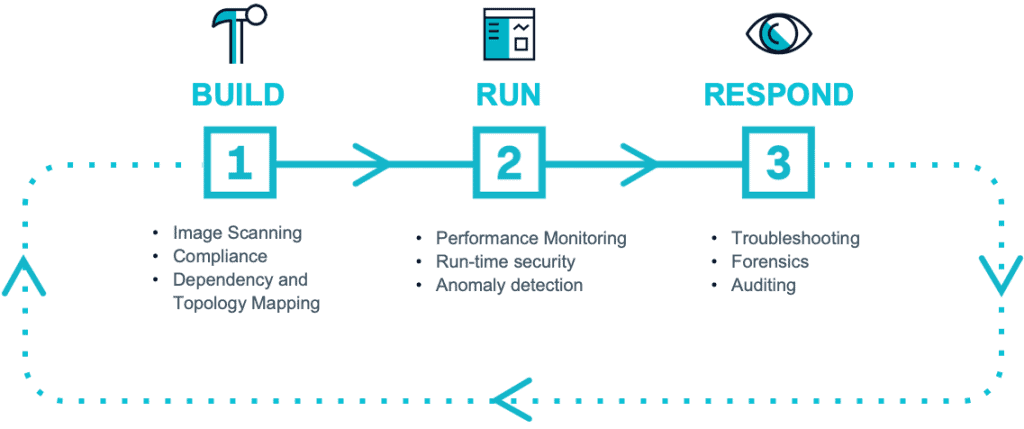
Build Run Respond Cycle
Below we have 3 demos that enable DevOps, security professionals, and service owners to reliably Build, Run, and Respond to critical issues with Kubernetes and containers in production. We trace the container lifecycle of applications through these 3 phases (Build, Run, and Respond).
Demo 1 [Build]: CI/CD Jenkins Pipeline with Sysdig Secure Scanning
This is the first demo in our 3-demo series. In this Build phase, we want to make sure that container images are scanned and free from vulnerabilities. We also need to include image scanning as a stage in our Jenkins or any other CI/CD pipeline. This ensures that developers are shifting security to the left and building with security in mind. If the image scanning fails, it fails early on in the development cycle so developers can respond appropriately and update their code and libraries used. We will work with a microservices app called the hipster app. It is developed by Google and it is very helpful in demonstrating an application that runs on a microservices framework. Below is a diagram showing the workflow that we use as part of this demo.
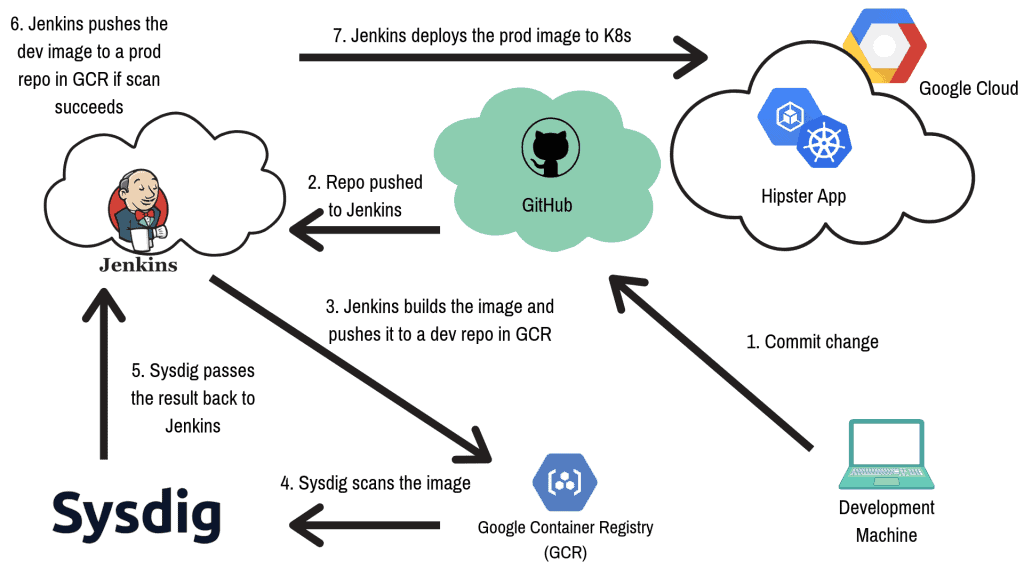
CI/CD Diagram with Sysdig Secure Image Scanning
Demo 2 [Run]: Performance Monitoring with Sysdig Monitor
In this demo, we move on to the Run phase. We talk about running our application. and specifically, discuss the need to monitor our application’s performance. Once again we work with the hipster app to demonstrate an application that runs on a microservices framework. First, we delete one of the deployments and see how Sysdig Monitor alerts us of HTTP 500 errors that show up. Then we’ll dig deeper by analyzing a Sysdig capture that was taken from the alert to get to the root cause.
Demo 3 [Respond]: Runtime Security with Sysdig Secure (MITRE ATT&CK)
In this final demo, we take a look at the Respond phase. The discussion is now about how to Respond to runtime security incidents. Sysdig created a mapping of Sysdig Falco policy rules to the MITRE ATT&CK matrix. The MITRE ATT&CK matrix is a framework that adversaries use in their attack chain. We assume the role of a hacker in this demo and run a few attacks against our environment. Sysdig Secure detects these attacks and defends against them. Finally, we analyze the forensics and dig deeper into the commands and the content of the malicious script that was run in our environment.
Conclusion
In this article and through the accompanying demos, we followed the life cycle of a microservices application through its 3 phases (Build, Run, and Respond). As enterprises move from legacy monolithic applications to adopt a microservices framework, there are new challenges that arise. It’s essential to have the right strategy and tools to help with these challenges. Sysdig manages the risk, health, performance, and security of systems and applications enabling organizations to be confident in their move to modernize their business operations.
References
- Hipster Demo App
- Sysdig Platform
- Falco
- MITRE ATT&CK matrix
- Sysdig blog about the Falco rules created around the MITRE ATT&CK matrix
Suggested Reading
- Jenkins, Vault, Terraform, Ansible, and Consul Delivering an End-to-End CI/CD Pipeline
- Hashicorp Packer, Terraform, and Ansible to Set Up Jenkins
- Webblog App Part 4 – HashiStack – Nomad Consul Vault Terraform
- HashiCorp Vault PKI Secrets Engine Demo for Certificate Management

