Introduction
In today’s ever-changing and complicated IT world, keeping secrets like API keys, passwords, and tokens safe and secure is crucial. HashiCorp Vault is a widely used solution that offers a secure central location for storing and accessing secrets. However, the challenge lies in securely introducing the Vault token, also known as Secret Zero, to machines outside of native management platforms like AWS. This article explores the Secret Zero problem, showcases the integration of HashiCorp Vault with AWS SSM Agent, and demonstrates how these tools can effectively handle and introduce secrets in multi-cloud settings.
Video
Below is a video explanation and demo.
Video Chapters
You can skip to the relevant chapters below:
- 00:00 – Introduction
- 00:41 – What is Secret Zero
- 01:39 – Establishing Trust
- 03:45 – Machines Outside of AWS
- 05:45 – Secrets Consumption Workflow
- 08:16 – Closing Remarks
Understanding the Secret Zero Problem
To grasp the Secret Zero problem, let’s draw an analogy to a popular password manager like LastPass. In LastPass, you need to know the master password to access your encrypted vault and retrieve other stored secrets. Similarly, in HashiCorp Vault, the Secret Zero is the Vault token that is essential for authentication and accessing stored secrets. However, the challenge lies in securely storing and accessing this Vault token itself, as it, too, is a secret. This creates a chicken-and-egg problem – how do you securely store the secret that grants access to other secrets?
Establishing Trust with Native Management Platforms
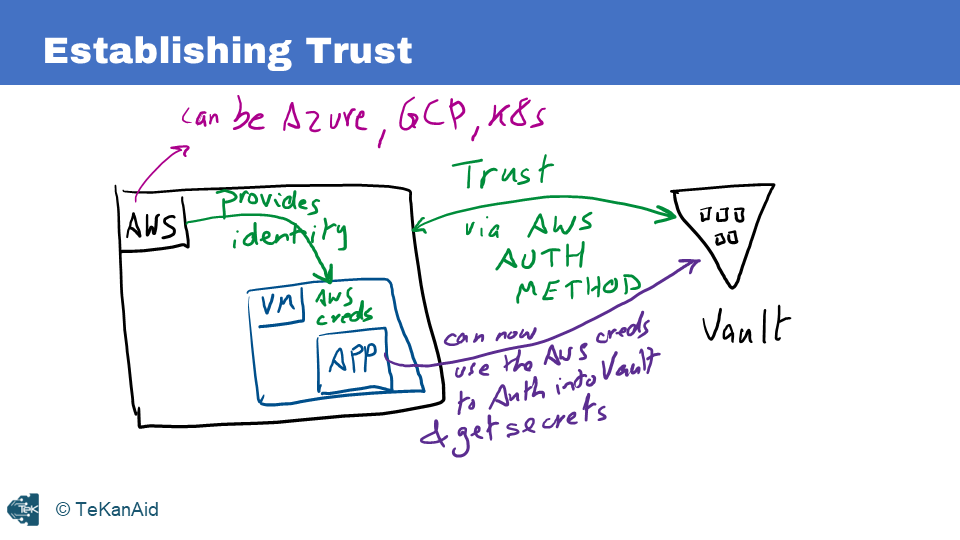
A straightforward solution to the Secret Zero problem arises when using a platform that Vault can trust, such as AWS, Azure, GCP, or Kubernetes. For instance, in the case of AWS, trust between Vault and the platform is established through the AWS authentication method. When AWS provisions resources like EC2 instances or Lambda functions, it assigns them unique identities and credentials. Applications running on these resources can leverage these credentials to authenticate with Vault. Vault, in turn, verifies the credentials with the AWS API to establish the identity and authenticity of the machine or application. This trust enables seamless retrieval of secrets from Vault without the need to store the Vault token externally.
Extending Trust to Non-Native Management Platforms
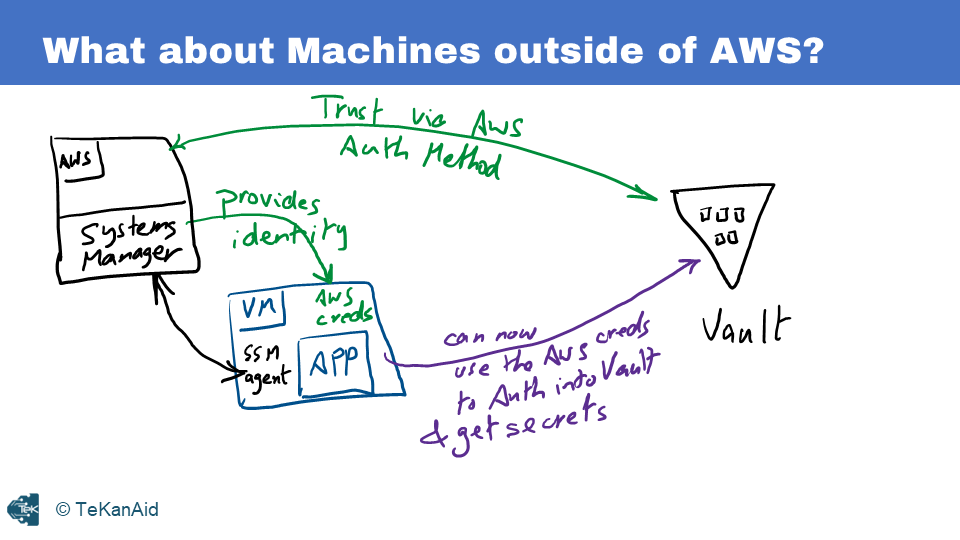
However, scenarios arise where machines reside outside the native management platforms, yet there is a need to establish trust and securely introduce the Vault token. One common example is a virtual machine (VM) running in an on-premises environment or on a platform like VMware vSphere. Here, the AWS SSM Agent comes into play. To grant an identity to machines outside of AWS, you can use the SSM Agent as a Systems Manager. Here’s how it works:
Here’s how it works
- Enable the AWS authentication method in Vault.
- Install and run the SSM Agent on the non-AWS VM.
- The SSM Agent communicates with Systems Manager to generate AWS credentials in a file.
- The non-AWS VM is now managed by AWS and has an identity within the platform.
- Applications within the VM can use these AWS credentials to authenticate with Vault, which verifies the credentials with the AWS API before allowing access to secrets.
Benefits of integrating AWS SSM Agent with Vault
The integration of AWS SSM Agent with HashiCorp Vault brings several benefits, including:
- Securely introduce secrets with the Vault token, also known as Secret Zero, to machines outside of the native management infrastructure. This decreases the chances of exposing secrets.
- secretSeamless Identity Management: The SSM Agent simplifies the process of obtaining AWS credentials and establishes an identity for the non-native VM within the AWS ecosystem, enabling authentication with Vault.
- Centralized Secret Management: Vault acts as a central repository for secrets, providing a secure and scalable solution for managing and accessing secrets across multi-cloud environments.
- Simplified Application Integration: With the help of Vault Agent, applications can retrieve secrets without the need for explicit Vault knowledge, reducing development effort and potential security vulnerabilities.
The Secrets Consumption Workflow
To illustrate the secrets consumption workflow, let’s consider the scenario where an AWS cloud interacts with a non-AWS VM (running in vSphere) using AWS SSM Agent and Vault Agent.

- The AWS SSM Agent periodically renews and updates AWS credentials in a file on the non-AWS VM.
- The application within the VM uses these credentials to authenticate with Vault via the AWS authentication method.
- The Vault Agent authenticates on behalf of the application, retrieving an application-specific token (app token) from Vault.
- The app token is stored securely in a sink file.
- The application uses the app token to authenticate with Vault and access the desired secrets.
- Alternatively, the Vault Agent can retrieve secrets on behalf of the application, eliminating the need for the application to be Vault-aware. This is accomplished by configuring a template file that renders secrets in a specific format for the application to utilize.
Conclusion
In modern IT operations, it’s crucial to secure secrets. The Secret Zero problem can be a challenge when using Vault tokens in multi-cloud environments. AWS SSM Agent and HashiCorp Vault can securely share secrets with external machines. This integration streamlines the authentication process and enables seamless access to secrets while centralizing secret management and enhancing overall security. By leveraging the power of these technologies, organizations can protect their sensitive data and ensure secure communication between applications and trusted secret repositories in multi-cloud environments.
For a better understanding of AWS SSM Agent and HashiCorp Vault configuration and implementation, we suggest checking out the HashiCorp Vault 202 for Operators course. It offers detailed concepts and practical deployment scenarios.

