Introduction
Introduction to Secure Software Development
Secure development has never been more important. Cyber attacks are getting more frequent and more sophisticated, targeting vulnerabilities at every stage of the software development lifecycle (SDLC). This guide covers the best practices and strategies for security and governance in development environments with Coder, focusing on three key features: Browser-Only Connections, Role-Based Access Control (RBAC), and Audit Logging.
This is our third and final blog post in our series exploring Cloud Development Environments with Coder. If you missed part one or two, I have links to these at the bottom of this post.
Video
Below is a video demonstration.
Video Chapters
- 00:00 Introduction to Enhancing Security and Governance with Coder
- 00:38 Overview of Key Security Features
- 00:56 Deep Dive into Audit Logging
- 01:35 Exploring Browser-Only Connections
- 03:18 Understanding Role-Based Access Control (RBAC)
- 04:03 Real-World Application: Discord’s Success Story
- 04:59 Demo: Implementing Security Features
- 05:27 Step-by-Step Guide: Enabling Browser-Only Connections
- 09:10 RBAC Configuration and Management
- 11:43 Comprehensive Audit Logs
- 14:51 Conclusion and Final Thoughts
What is Secure Development?
Secure development is a methodology that embeds security into every stage of the SDLC. This means protecting software from cybercriminals and hackers, minimising security vulnerabilities and user data. Security can’t be an afterthought, it has to be part of the development process.
Benefits of Security in the Software Development Lifecycle
Security in the SDLC helps to identify and fix potential security threats and weaknesses early in the software development process. This proactive approach reduces the risk of security breaches, improves the overall quality of the software and compliance to regulatory requirements. It also creates a security aware culture in the development teams.
Software Security Risks
Several things contribute to software security risks:
- Interconnected Systems: Software is built on top of multiple systems. One system can affect the others.
- Software Size and Complexity: Larger and more complex software is harder to test thoroughly, more likely to have security vulnerabilities.
- Outsourced Software Supply Chain: Relying on third-party vendors can introduce more risks if not properly vetted.
Secure Software Development Lifecycle (SSDLC)
Let’s take a look at the phases of a secure software development process.
Planning: Set Security Goals & Objectives
The first phase of SSDLC is to define security requirements using relevant security policies. This phase is to identify potential security threats and weaknesses and set clear security goals and objectives.
Design: Identify Security Controls & Architect the Product
In the design phase, security controls and components are identified to meet security requirements. This phase is where critical decisions are made that will impact the security of the software, such as implementing secure authentication and data encryption.
Implementation: Write Secure Code, Static Analysis & SCA
Writing secure code is part of the SSDLC. Developers must follow security requirements and use security controls. Static code analysis (SCA) tools can help identify security flaws in the code early in the development process so teams can fix them.
Verification: Code Reviews & Dynamic Analysis
The verification phase is to validate that security requirements are implemented correctly without introducing new security issues. This phase includes manual code reviews, automated test cases and dynamic analysis to ensure security controls are in place.
Maintenance: Security Monitoring & Patching
Security is an ongoing process. Regularly reviewing and updating security controls is required to address new and emerging security issues. Security patches may be required to fix specific security vulnerabilities to keep the software secure throughout its life.
Secure Software Development Practices
Developing secure software should be everyone’s responsibility and not just the security team’s.
Secure Coding Guidelines and Standards
Every organization should have its own set of secure coding guidelines. These guidelines help developers to write secure code by providing best practices and standards. For example, encryption services should be used to protect sensitive data, to encrypt data at rest and in transit.
Code Integrity
Code integrity is key. All code should be in secure repositories and access should be restricted to authorized personnel only. This prevents unauthorized changes and ensures the code is trustworthy. But this can be tricky when you outsource some of your development work to third-party vendors. These development teams will have your company’s code on machines outside your environment. Check out browser-only connections from Coder below.
Review and Test Code Early and Often
Breaking away from the traditional development pattern of security testing code at the end of the SDLC is essential. Both developer reviews and automated testing should be used to continually examine code for flaws, ensuring that security is integrated from the start. I’m a big advocate of Agile development with security incorporated in every sprint.
Coder’s Security Features
Now let’s get into the nitty gritty and look at the security features Coder offers.
Turn on Browser-Only Connections
The first practical way to improve security and governance is to turn on browser-only connections. This is especially important for regulated and highly secure industries like financial services, defense, and intelligence, where centralized approval for developers to install local tools can delay productivity.
To enable browser-only connections, update the environment variables in your values.yaml file for your Coder helm chart. Split the values into two files: secrets.yaml and values.yaml, with a secrets.example.yaml for your reference. Ensure that sensitive information in secrets.yaml is not pushed to GitHub.
Add the following line to secrets.yaml:
coder_browser_only: true
Upgrade your Helm chart and browser-only connections will be turned on. Check this by going to deployments under the security section in your Coder interface.
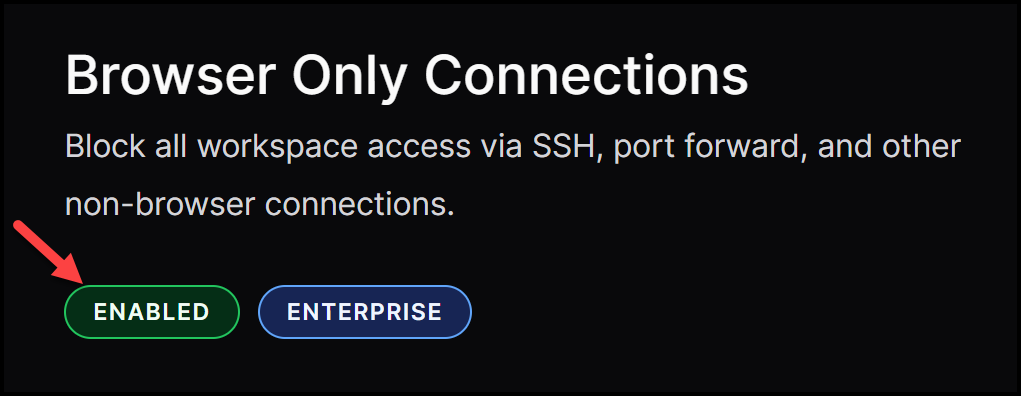
When you create a workspace you will see that only web-based tools like Code Server and terminals are available, so local IDEs can’t be used.
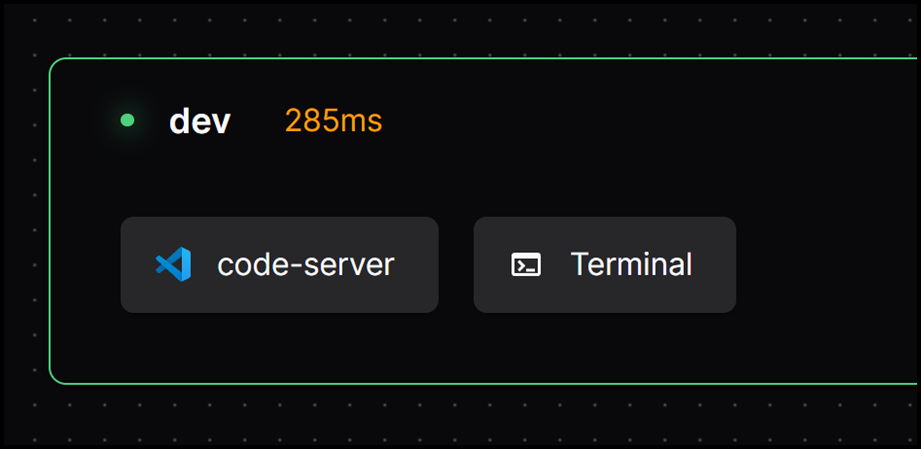
This reduces the risk of code exfiltration by keeping the code in your controlled environment and only accessible through secure browser-based connections.
Browser-only connections improve security and simplify development. Developers can start coding straight away without waiting for approval to install local tools, speeding up the development process and project timelines. The browser-based approach also means developers always use the latest version of their tools, reducing compatibility issues and overall efficiency.
Another benefit of browser-only connections is the reduced attack surface. Since developers don’t need to install or configure local development environments, the risk of introducing vulnerabilities through misconfigured tools or outdated software is minimized. This controlled environment means all development activity is done in a secure, standardized environment.
Turn on RBAC for Templates
Now let’s turn on Role-Based Access Control (RBAC) to manage access to templates and other resources in your development environment. RBAC is a key feature that allows you to define which users and groups can use which templates so only authorised personnel have access to critical resources.
RBAC Configuration and Management
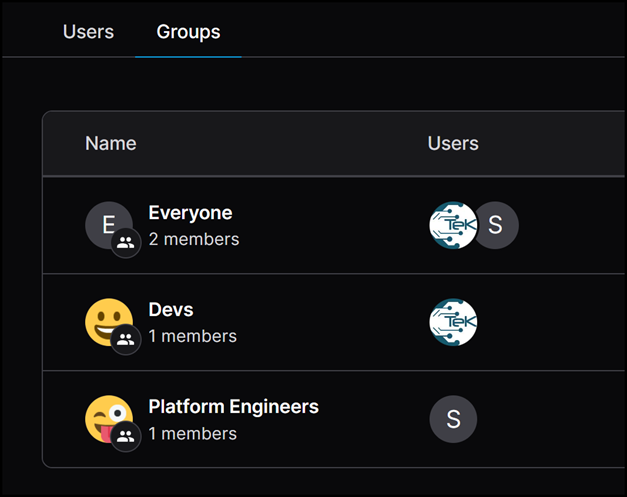
Under users in Coder, create and manage groups like “Devs” and “Platform Engineers.” Assign roles and permissions to these groups. For example, platform engineers can have access to certain templates, while developers can only use other pre-defined templates.
In the templates section define permissions for each template. For example, you can allow the platform engineers group to use and manage a specific template but restrict other groups to only use it and not modify it.
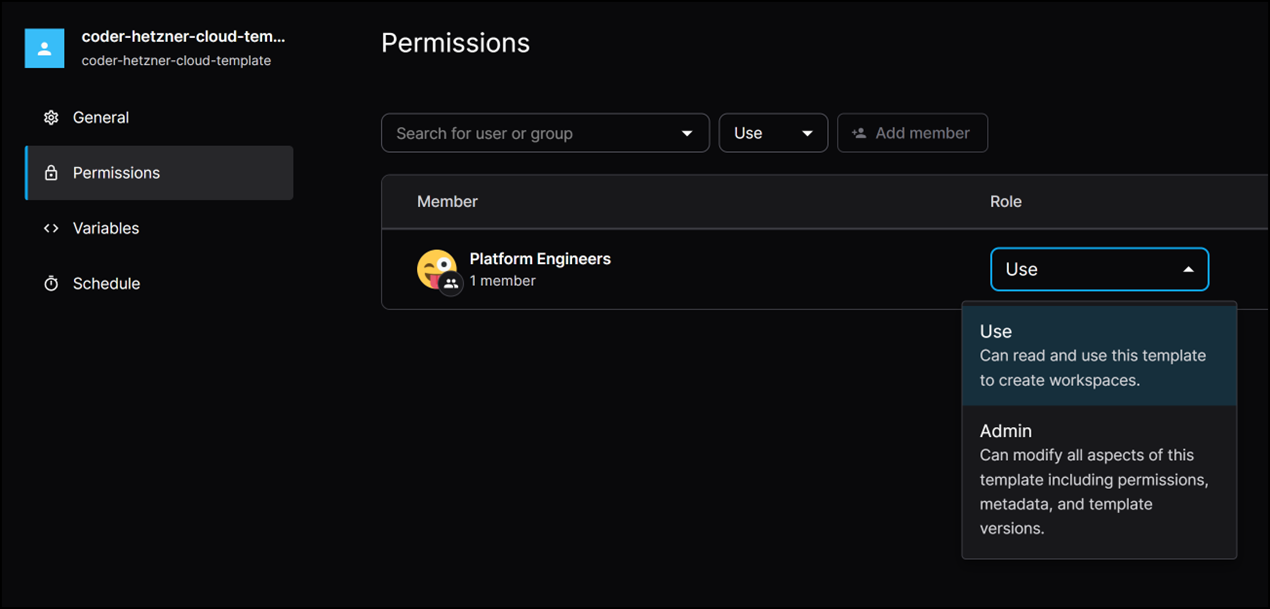
RBAC ensures access to critical resources is controlled and monitored and a secure and organised development environment.
RBAC also makes onboarding new team members easier. By adding them to the right groups new developers can get access to the tools and resources they need to start coding straight away. This speeds up downtime and gets new team members productive faster.
Also, RBAC’s fine-grained permissions allow for tuning of access rights. For example you can create sub-groups within larger teams to handle specific tasks or projects, each with their own set of permissions. This means access controls can be tailored to your organization’s specific needs.
One of the main benefits of RBAC is that it enforces the principle of least privilege. By restricting access to only what’s needed for a user’s role, organisations can reduce the risk of accidental or malicious data breaches. For example, developers working on front-end components don’t need access to back-end databases, and RBAC ensures they can’t access those sensitive areas.
RBAC also enables collaboration by defining roles and responsibilities. Teams can be grouped with specific permissions so everyone knows their access rights and responsibilities. This clarity reduces errors and overall productivity.
Also, RBAC can be integrated with your existing identity providers like Okta or Azure AD so you can sync user roles and permissions seamlessly. This integration makes user management and access control across all systems consistent.
Review Audit Logs
Finally reviewing audit logs is key to security and compliance in your development environment. Audit logs provide transparency and accountability so you can see who did what and when.
Full Audit Logs
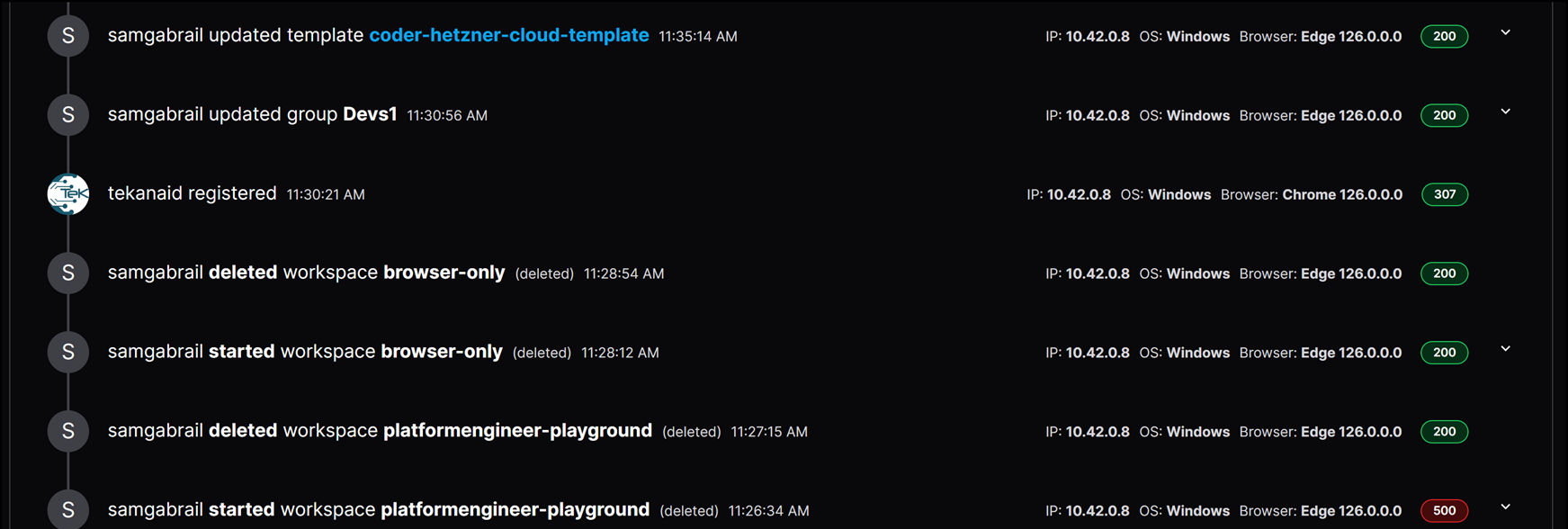
Go to the audit logs section in Coder to see all activity. You can filter logs by resource types, actions, and users. Audit logs capture detailed activity by each user, recording the origin, device, browser, and status code of every interaction. This gives you a full audit trail of activity for security and compliance.
Audit logs can be filtered for more detail and the data can be exported to external tools like Splunk for further analysis. This is required for compliance and to ensure all activity in the development environment is logged and reviewable.
Audit logs are also important for post-incident analysis. In the event of a security breach, detailed logs will provide valuable information to help you identify the root cause, understand the impact, and develop strategies to prevent future incidents. This forensic capability is key to a secure and resilient development environment.
Also, regular review of audit logs can help identify patterns of behavior that may indicate security risks. For example, repeated failed login attempts or unusual access patterns can be early indicators of a compromised account. By monitoring audit logs proactively, security teams can take preventative measures to protect the organization’s assets.
One of the benefits of Coder’s audit logging is real-time visibility into user activity. Real-time monitoring is key to detecting security breaches or unauthorized access. For example, if an unauthorized user tries to access sensitive code repositories, the audit logs will record this activity immediately so security teams can act fast.
Also the logs are detailed—IP addresses, browser types, status codes etc—so you can investigate any suspicious activity. This level of detail is important for forensic analysis in the event of a security incident.
Audit logs in Coder can also be accessed via a REST API so you can integrate with other systems like Splunk and various Security Information and Event Management (SIEM) tools. This means all logs are centralized and can be monitored for suspicious activity or compliance checks.
Real-World Application: Discord’s Success Story

Discord is a great example of how Coder’s security features can be used in the real world. As a polyglot development environment, Discord uses multiple languages and supports all major platforms. Moving to Coder brought enhanced security features, including built-in identity and access management.
Running on EC2 instances in AWS, Discord used Coder to ensure the immutability and reproducibility of their development environments. They also adopted Tailscale and WireGuard in Coder’s v2 to improve their networking stack and obtain more stable and secure connections.
By using Coder, Discord was able to standardize their development environments so that all projects were consistent. This standardization reduced the time spent on setting up and managing development tools, so developers could focus on writing code. Also, the built-in identity and access management provided an extra layer of security so that only authorized users could access critical resources.
Tailscale and WireGuard added an extra layer of security by encrypting the connections between developers and their workspaces. This secure networking solution minimized the risk of data interception and ensured all communication was protected from threats.
You can read more about Discord’s success story here.
Conclusion and Final Thoughts
In this post, we talked about software security risks and some secure coding practices. We also explained how to perform secure software development to address security vulnerabilities at a high level.
Then we focused on how Coder enhances security and governance in development environments through centralized control. We covered three main features: Browser-Only Connections, Role-Based Access Control, and Audit Logging. We also discussed Discord’s success story in adopting Coder.
Coder’s robust security features can significantly enhance the way your software developers work, ensuring that your code and intellectual property are secure. By implementing these features, organizations can achieve a higher level of security and compliance, protecting their valuable assets from potential threats.
Try Coder out for yourself. Its security and governance features will change the way you develop. Thanks for reading, and I hope you found this helpful. Stay safe and happy coding!
Suggested Reading
- Create a Cloud Development Environment with Coder | Part 1/3
- Optimize Cloud Development Costs with Coder | Part 2/3
Code
Hi and Welcome!
Join the Newsletter and get FREE access to all my Source Code along with a couple of gifts.

