Introduction
As we continue to move faster with application development, securing secrets has never been more critical. The increasing number of machines, applications, and environments requiring secure access has led to a significant rise in the number of secrets—API keys, credentials, certificates—that need to be protected. However, with this growth comes the challenge of managing these secrets effectively and securely.
Video
Below is a video demonstration.
Video Chapters
-
00:00 Introduction
-
00:49 DFC Technology
-
01:39 Architecture Diagram
-
02:18 Demo Starts
-
07:11 Create an Encryption Key using the Customer Fragment
-
08:51 Can we see the secret from the SaaS Backend?
-
09:48 Testing from outside the Network
-
10:39 Enable Zero-Knowledge Encryption on All Secrets
-
11:39 Wrap-up
The Challenge of Secrets Management
The move to the cloud has introduced complexities that many organizations struggle to manage. One of the primary challenges is secrets sprawl—the proliferation of secrets across various environments, often with little to no visibility or control. Security professionals frequently face the dilemma of not knowing how many secrets exist within their organization or where they are stored. This lack of visibility can lead to significant security vulnerabilities.
Secrets are often embedded in code or configuration files, making them prime targets for hackers. Without a robust secrets management system and proper access management, organizations risk exposing these sensitive pieces of information to unauthorized access, leading to potential data breaches.
Managing secrets through traditional vaults can also be cumbersome, diverting focus from the critical task of securing the secrets themselves. Vault management often becomes a bottleneck, adding unnecessary complexity and overhead to the security process. The challenges and inefficiencies associated with managing vaults highlight the need for a more streamlined, ‘vaultless’ solution.
Why Customers Choose Akeyless
Akeyless has quickly become a preferred choice for businesses looking for robust secrets management solutions. The reasons behind this are clear:
- Ease of Management with High Availability: Akeyless operates as a Software as a Service (SaaS) platform, ensuring that secrets management is both easy to handle and highly available. The SaaS model means that businesses don’t need to worry about the infrastructure, as Akeyless takes care of it, offering seamless management with minimal effort.
- Reduced Total Cost of Ownership: As businesses grow and scale, the need to add more infrastructure typically increases costs. However, Akeyless provides a cost-effective solution that scales without requiring additional clusters, significantly reducing the total cost of ownership.
- One Integrated Solution: Akeyless isn’t just about secrets management. It also offers secure remote access, password management, and encryption with Key Management Service (KMS) capabilities. This all-in-one solution simplifies operations and strengthens security across various facets of an organization’s digital infrastructure.
But one of the first questions you might ask is, “How can I trust a SaaS offering with my secrets?” This is a valid concern, and Akeyless addresses it with its innovative technology and stringent security protocols.
Introducing Akeyless’s Distributed Fragments Cryptography (DFC)
Akeyless offers a groundbreaking solution to the challenges of secrets management with its Distributed Fragments Cryptography (DFC) technology. This patented innovation provides a secure and unified platform for managing credentials, certificates, and encryption keys without the need for traditional vaults.
DFC technology is designed for the modern, cloud-native environment, making it ideal for hybrid and multi-cloud setups. By eliminating the need for vaults, Akeyless not only simplifies the management of secrets but also enhances security by ensuring there is no single point of breach. This approach allows for infinite scalability while significantly lowering the total cost of ownership.
DFC: The Heart of Akeyless Security
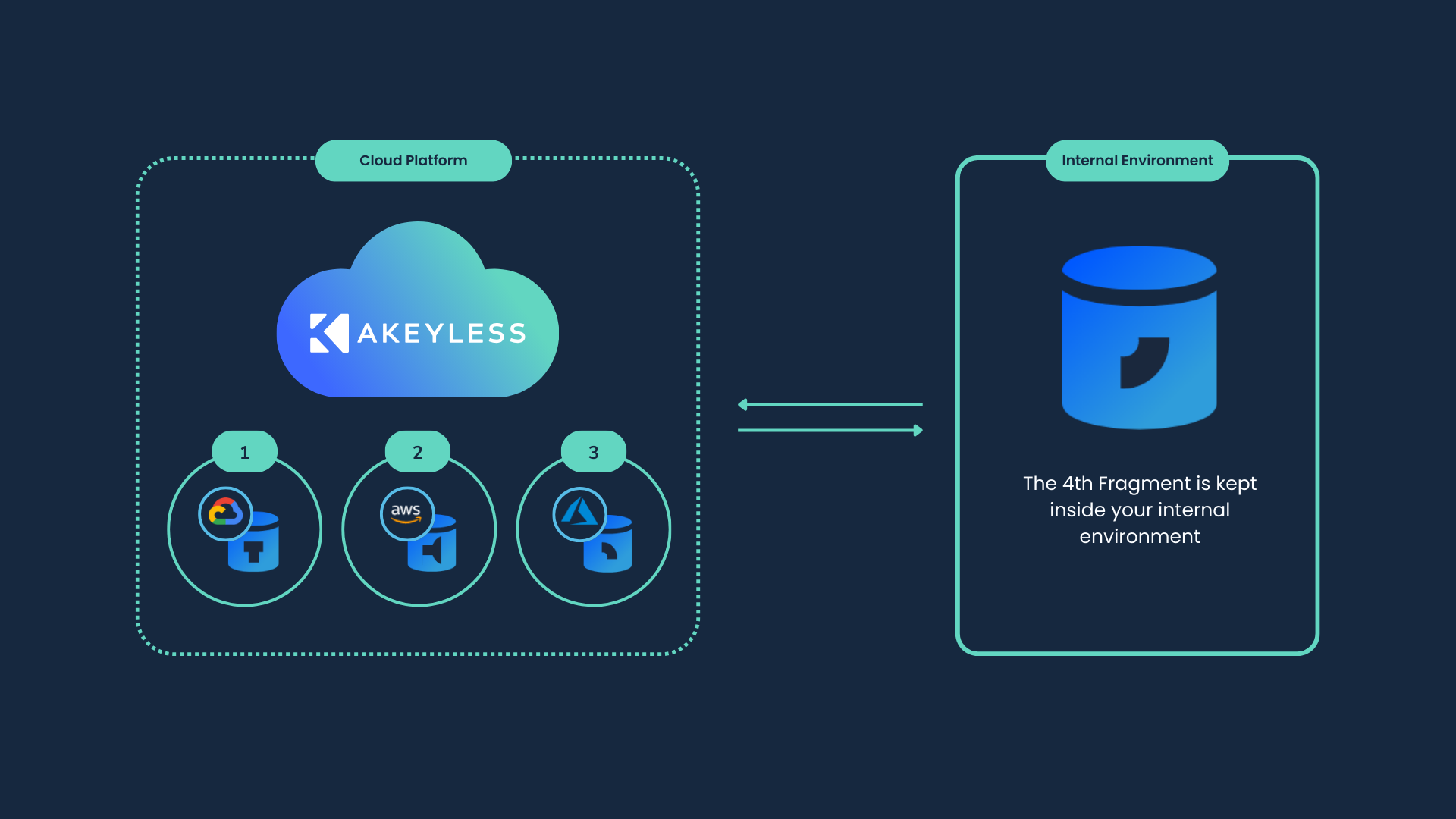
Now let’s see how DFC works:
- Fragmented Encryption Keys: DFC enables the use of fragments of an encryption key without ever combining them. This means that even though parts of the key are stored in different regions or cloud providers, the full key never exists in a single location, making it incredibly difficult for attackers to gain access.
- Triple-Layer Security: For an attacker to access your secrets, they would need to simultaneously attack all three cloud providers where the key fragments are stored—a nearly impossible task, adding an extra layer of security.
- Dynamic Secret Creation: DFC supports dynamic secret creation, which enhances secret rotation and overall efficiency in managing sensitive information. This feature automates the generation and rotation of secrets, reducing the risk of exposure and ensuring that your security processes remain robust and up-to-date.
- Zero-Knowledge Encryption: To further enhance security, Akeyless allows you to create your own customer fragment. This fragment is a critical piece of the encryption key that only you hold. With zero-knowledge encryption, not even Akeyless can view your secrets. However, this also means that if you lose this fragment, there’s no way to recover your data, emphasizing the importance of secure storage.
Understanding the Akeyless Architecture
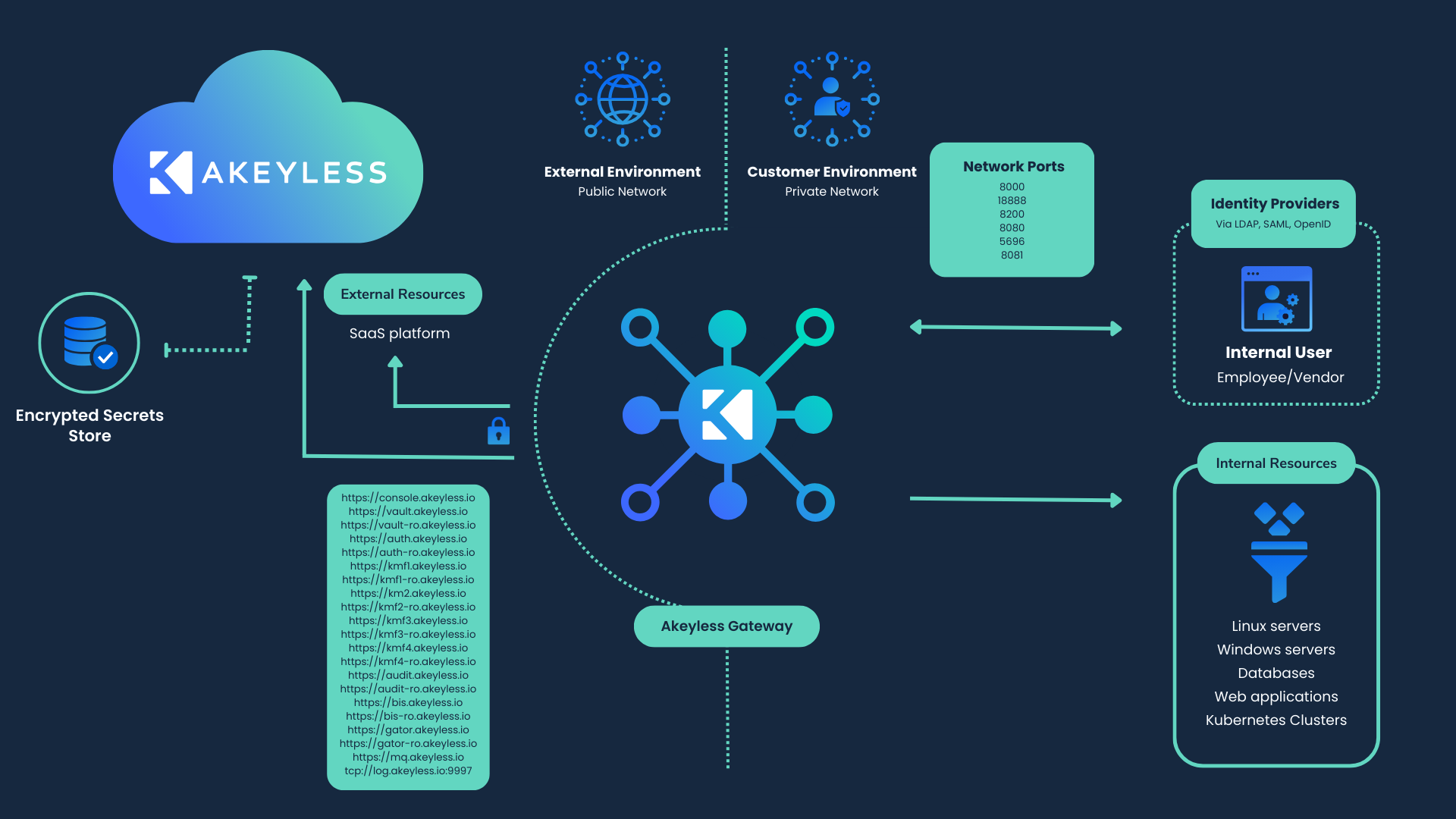
Akeyless’s architecture is designed to provide flexibility and security, ensuring that your secrets are protected whether they’re stored on-premises or in the cloud. It offers a comprehensive platform to manage credentials, providing DevOps and Infosec teams with a unified and secure approach to handling sensitive information such as credentials, certificates, and keys. The architecture is divided into two main sections:
- Public Network (External Environment): This is where the Akeyless console, or SaaS, operates. It manages the interaction between users and the secrets stored within the system.
- Private Network (Internal Environment): Here, the Akeyless gateways operate. These gateways can be deployed on-premises, within your Virtual Private Clouds (VPCs), or across different cloud providers like AWS, Azure, and Google Cloud Platform (GCP). Internal users, employees, and vendors can access the secrets by communicating directly with the Akeyless gateway.
This setup ensures that secrets are accessible to those who need them while remaining secure from external threats. The gateway acts as a secure bridge between your internal systems and the Akeyless SaaS, ensuring that your secrets are always protected.
Real-World Applications
Let’s explore some real-world applications of DFC:
- Managing Access to Cloud Resources: Use Akeyless as a secrets manager to provide a centralized solution for managing sensitive information, such as API keys and credentials. This ensures that only authorized users can interact with sensitive data while maintaining data isolation and access control.
- Temporary Access for Third-Party Vendors: Provide temporary access to secrets for third-party vendors or contractors, controlling and monitoring their access to your systems.
- Multi-Cloud Secrets Management: Seamlessly manage secrets across multi-cloud environments, ensuring consistent security practices regardless of the cloud providers in use.
Hands-On with Akeyless: A Demo Walkthrough
To truly understand the power and simplicity of Akeyless, let’s walk through a demo scenario where we create and manage a gateway, generate customer fragments, and use these to encrypt secrets.
Step 1: Creating a Gateway
The first step in using Akeyless is to create a gateway. This gateway will serve as the point of access for your internal users and systems. The process is straightforward:
- Choose Your Deployment Method: You can deploy the gateway using Docker or Kubernetes. In this demo, we’ll use Docker. After running the necessary commands, the gateway will be up and running.
- Secure Your Customer Fragment: Before proceeding, it’s essential to create a customer fragment. This fragment will be stored securely and is critical for enabling zero-knowledge encryption. Once created, it must be safeguarded carefully, as losing it would result in the inability to decrypt your data.
- Run the Gateway: With the customer fragment in place, you can start the gateway. The gateway will connect to the Akeyless SaaS backend, ensuring that your secrets are accessible through a secure connection.
Step 2: Configuring the Gateway and Connecting to the SaaS Backend
Once the gateway is running, you’ll need to configure it and ensure it communicates properly with the Akeyless SaaS backend:
- Gateway Configuration UI: Access the gateway’s configuration UI through your browser. Here, you can monitor the gateway’s health, ensure it’s connected to the SaaS backend, and make any necessary adjustments.
- Setting Up Zero-Knowledge Encryption: The customer fragment you’ve created will be integrated into the gateway configuration. This enables zero-knowledge encryption, ensuring that your secrets remain secure and inaccessible to anyone outside your organization.
Step 3: Creating an Encryption Key
With the gateway configured, the next step is to create an encryption key using the customer fragment:
- New Encryption Key: In the Akeyless console, create a new encryption key and select the DFC (Distributed Fragments Cryptography) option. Name the key and assign it to the appropriate folder.
- Zero-Knowledge Encryption: The customer fragment will automatically be applied to the new encryption key, ensuring that it is protected by zero-knowledge encryption. This means that even Akeyless cannot access the encrypted data.
Step 4: Creating and Managing Secrets
Now that you have an encryption key, you can create and manage secrets:
- Creating a Secret: Choose a secret type (e.g., static secret) and encrypt it using the zero-knowledge encryption key you created. The secret will be stored securely, and you’ll see an indicator showing that it is protected by zero-knowledge encryption.
- Accessing Secrets: You can access the secret through the gateway. However, if you attempt to access the secret from outside the network where the gateway resides, you’ll encounter an error, demonstrating that without the customer fragment, the secret cannot be decrypted.
Testing and Verifying Security
One of the critical tests is to ensure that Akeyless truly operates with zero-knowledge encryption. To do this, we’ll attempt to access the encrypted secret from outside the network:
- VPN Outside the Network: By connecting to a network outside of where the gateway is located and attempting to access the secret, you’ll see an error message stating that the customer fragment is required but not available. This confirms that without the customer fragment, the secret cannot be decrypted, ensuring that your data remains secure.
Enabling Zero-Knowledge Encryption Across All Secrets by Default
Akeyless allows you to use zero-knowledge encryption across all secrets by default, ensuring that all sensitive data is protected by the highest level of security:
- Default Encryption Key: In the gateway configuration console, you can set the default encryption key to the zero-knowledge encryption key you created. This ensures that all secrets, whether dynamic or static, are encrypted using the customer fragment.
- Seamless Security: With zero-knowledge encryption enabled by default, all new secrets will automatically be protected, giving you peace of mind that your data is secure.
Conclusion: Trusting Akeyless for Secure Secrets Management
Akeyless’s Distributed Fragments Cryptography (DFC) technology represents a significant advancement in secure secrets management. By eliminating the need for vaults and providing a scalable, cloud-native solution, Akeyless ensures that organizations can manage their secrets with confidence.
Whether you’re a security professional, Platform engineer or DevOps engineer, Akeyless offers a unified platform that simplifies secrets management while enhancing security. With Akeyless, you can focus on what truly matters—protecting your organization’s most sensitive data in a secure and efficient manner.
In conclusion, Akeyless’s DFC technology is the ideal solution for organizations looking to streamline their secrets management process, reduce the risk of secrets sprawl, and ensure that their sensitive data is always protected, no matter where it resides. Give it a try!
Suggested Reading
- Secure Platform Engineering with Akeyless Workshops
- Build an Internal Developer Platform with GitOps: Part 1
Code
Hi and Welcome!
Join the Newsletter and get FREE access to all my Source Code along with a couple of gifts.

